2K Games Discloses Startling Security Breach, Tells Players Not To Open Support Emails

2K, the publisher of numerous video game series, including Borderlands, Civilization, and Bioshock, has issued a notice to warn customers that an unknown actor recently gained unauthorized access to its help desk platform. The threat actor in question abused this access to distribute malware by way of the 2K Games support email address. The publisher’s notice emphatically states, “Please do not open any emails or click on any links that you receive from the 2K Games support account.” For those who may have clicked on a malicious link sent by the 2K Games support email address, we offer some recommended actions down below.
This security breach comes on the heels of a data breach at Rockstar Games, the developer of the Grand Theft Auto (GTA) franchise. Both Rockstar Games and 2K are owned by Take-Two Interactive, which makes us wonder whether the 2K security breach is related to the Rockstar Games breach. For those unfamiliar with the latter, an unknown actor recently stole GTA 6 gameplay footage from Rockstar Games and published it on the public forums for the franchise. The hacker also claims to have stolen source code for both GTA 5 and 6. While the actor behind this data breach is currently unknown, he claims to be the same actor behind the recent Uber security breach, who Uber believes to be associated with the LAPSUS$ hacking group.
This security breach comes on the heels of a data breach at Rockstar Games, the developer of the Grand Theft Auto (GTA) franchise. Both Rockstar Games and 2K are owned by Take-Two Interactive, which makes us wonder whether the 2K security breach is related to the Rockstar Games breach. For those unfamiliar with the latter, an unknown actor recently stole GTA 6 gameplay footage from Rockstar Games and published it on the public forums for the franchise. The hacker also claims to have stolen source code for both GTA 5 and 6. While the actor behind this data breach is currently unknown, he claims to be the same actor behind the recent Uber security breach, who Uber believes to be associated with the LAPSUS$ hacking group.
Now, not even a week after the Rockstar Games breach, a threat actor accessed the 2K help desk and used it to send out phishing emails. Normally phishing emails are sent from an email address at a domain name that looks similar to that of a legitimate company or website to trick users into believing the email was sent by a legitimate source. However, threat actors don’t need to bother with this technique if they can send emails directly from the email address of a legitimate company.
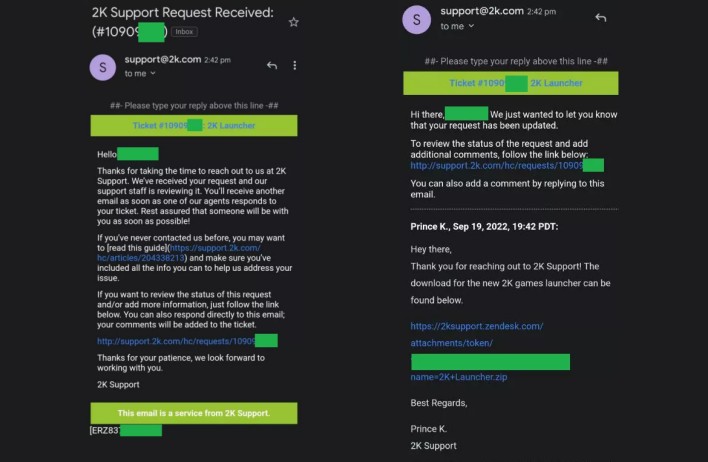
The emails sent by the threat actor using the support@2k.com email address provide updates on the status of a fake support ticket. An initial email informs recipients that the support request is under review. A second email then directs recipients to download a file presented as a new 2K Games launcher application. The file, named 2K+Launcher.zip, installs the RedLine stealer malware, which swipes all sorts of personal information from infected computers, including system information, browser history, cookies, credit card information, cryptocurrency wallet information, and login credentials stored in web browsers.
The emails sent by the threat actor using the support@2k.com email address provide updates on the status of a fake support ticket. An initial email informs recipients that the support request is under review. A second email then directs recipients to download a file presented as a new 2K Games launcher application. The file, named 2K+Launcher.zip, installs the RedLine stealer malware, which swipes all sorts of personal information from infected computers, including system information, browser history, cookies, credit card information, cryptocurrency wallet information, and login credentials stored in web browsers.
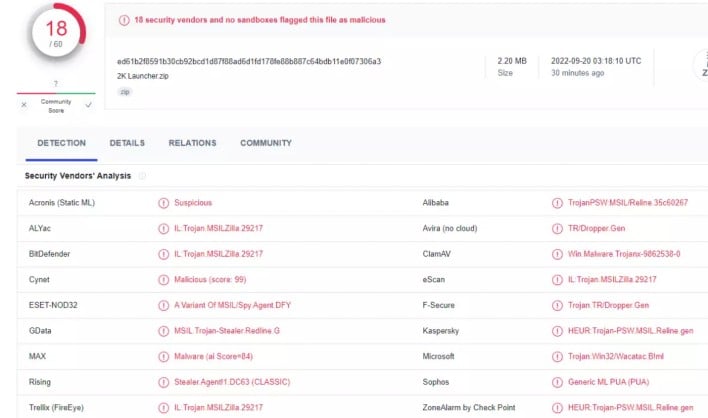
Anyone who recently opened an email from 2K Games support and downloaded a file can take a number of steps to check for malware and secure their accounts. The easiest check users can perform is to visit the VirusTotal website and upload any files they may have downloaded from a link displayed in a 2K Games support email. VirusTotal can scan the file using over 70 different antivirus scanners to check for a malicious payload.
Users can also check their systems for the presence of malware with an antivirus scanner like Malwarebytes. Malwarebytes offers a free application for both Windows and Mac that is easy to install, use to run a full scan, then uninstall.
Users can also check their systems for the presence of malware with an antivirus scanner like Malwarebytes. Malwarebytes offers a free application for both Windows and Mac that is easy to install, use to run a full scan, then uninstall.
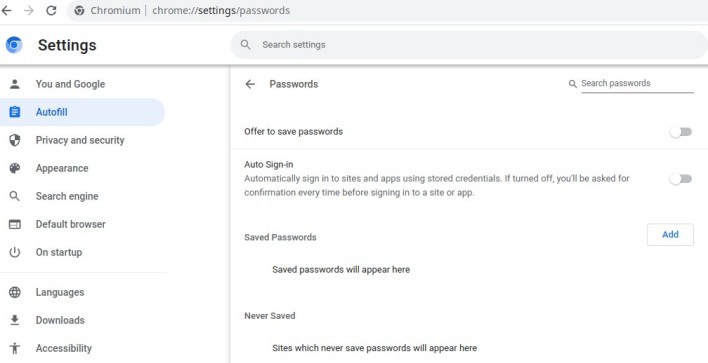
Users should also check their browsers to see whether there are any saved passwords, addresses, or credit card credentials, as the RedLine stealer malware can read and exfiltrate this information. Users can check for saved passwords in Chromium-based browsers, such as Chrome and Brave, by entering chrome://settings/passwords into the address bar. Users can do the same in Firefox-based browsers by entering about:logins. Users can also check for saved credit card information and addresses by visiting chrome://settings/autofill in Chromium-based browsers and Settings > Privacy & Security > Forms and Autofill > Saved Addresses/Saved Credit Cards in Firefox-based browsers.
Users who recently received emails from 2K Games support may want to setup multi-factor authentication (MFA) and change the login credentials for any services for which login credentials are stored in the users’ browsers. These same users may also want to freeze their credit if credit card information is stored in their browsers. Finally, users should check their email accounts and clients to make sure that there aren’t any new rules forwarding their email to unfamiliar email accounts. Check with your email provider for the exact process to accomplish this.
The 2K notice informing customers of the security breach tells customers that the publisher will “issue a notice when you can resume interacting with official 2K help desk emails,” so watch the 2K Support Twitter account for a further notice before interacting with 2K support over email any further.
Top Image courtesy of Dominik Deobald
Users who recently received emails from 2K Games support may want to setup multi-factor authentication (MFA) and change the login credentials for any services for which login credentials are stored in the users’ browsers. These same users may also want to freeze their credit if credit card information is stored in their browsers. Finally, users should check their email accounts and clients to make sure that there aren’t any new rules forwarding their email to unfamiliar email accounts. Check with your email provider for the exact process to accomplish this.
The 2K notice informing customers of the security breach tells customers that the publisher will “issue a notice when you can resume interacting with official 2K help desk emails,” so watch the 2K Support Twitter account for a further notice before interacting with 2K support over email any further.
Top Image courtesy of Dominik Deobald