AMD And NVIDIA GPUs Are Shockingly Being Used To Secretly Store Sophisticated Malware
Do you ever feel like the universe just has it in for you? Adding to the theory that some entity is pulling the strings from behind the scenes and having a good chuckle at our expense, not only are graphics cards frustratingly almost always out of stock (and overpriced), but if you do manage to procure one, you may have to worry about it being infected with malware. It doesn't even matter if you opt for an AMD or NVIDIA graphics card. Or use integrated Intel graphics, for that matter.
Sure, things could certainly be worse, and this falls under the purview of another first-world problem, but that's part of what we cover around these parts. And much to our chagrin, someone on a dedicated forum for hackers appears to be hawking a proof-of-concept (PoC) that can hide malicious code in a GPU, away from the watchful eyes and protection of security solutions that scan systems and RAM.
This is not a new concept, and within the academic world, demos of similar techniques have been disclosed in the past. Some of these have been incomplete and/or lacking much polish. But what's different here is that a working technique is actively being shopped to hackers, potentially opening up a whole new level of attack attempts.
According to BleepingComputer, which has seen the forum post, someone in the thread pointed out that a GPU rootkit called JellyFish swam to the surface more than half a decade ago, as a PoC. The researchers behind JellyFish also disclosed a couple of other potential GPU exploits, including a keylogger and a remote access trojan (RAT). The published reports have all been publicly accessible since 2015.
This latest technique is different, though, according to seller, who apparently has already found a buyer. If both of those claims are true, then this could potentially spell bad news, at least for Windows users—apparently it only works in Windows that support OpenCL 2.0 or later.
The listing states this supposedly new method infests the GPU memory buffer to inject and execute malicious code. They also claim to have tested the PoC on a variety of GPUs, including NVIDIA's GeForce GTX 1650 and GeForce GTX 740M, AMD's Radeon RX 5700, and Intel's UHD 630 and UHD 620.
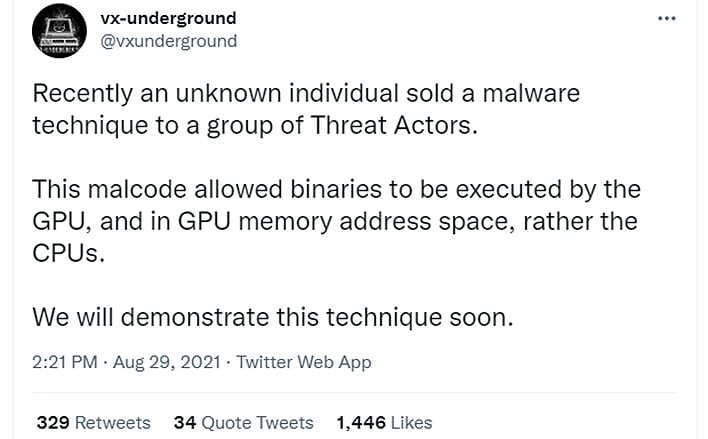
Is the threat credible? Unfortunately, it just might be. The folks at VX-Underground, which maintains the largest collection of malware source code, samples, and papers on the planet, suggested in a Twitter post that it does indeed work, and they plan to prove it.
"Recently an unknown individual sold a malware technique to a group of Threat Actors. This malcode allowed binaries to be executed by the GPU, and in GPU memory address space, rather the CPUs. We will demonstrate this technique soon," they tweeted.
Here's hoping that if GPU-based malware does become a legitimate threat, that GPU makers and security providers will both make quick work of neutralizing the threat.