This Android Banking Malware Steals Your Logins And Then Leaves Ransomware Surprise

An Android banking Trojan with an already extensive toolkit recently gained a ransomware module. While banking malware is an all too prevalent a threat for mobile devices, ransomware isn’t a technique commonly deployed against mobile devices, making this particular piece of malware notable. Banking Trojans come in the form of malware-laden apps that pose as legitimate apps in order to trick unsuspecting users into installing them. Once installed, the malware steals information, especially user credentials for banking and other financial services, then uploads that information to a command-and-control (C2) server controlled by the threat actor behind the attack.
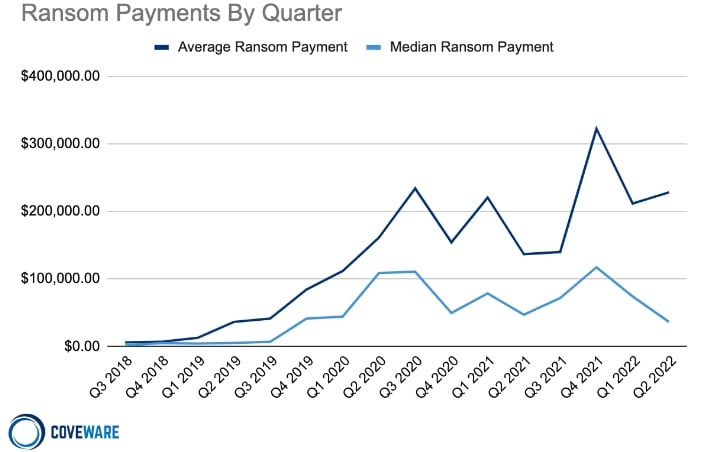
Ransomware encrypts files on infected devices with encryption keys known only to the attacker, rendering the files inaccessible to the victims. The attacker then extorts the victims by asking them to pay ransom fees to have their data unencrypted. Ransomware gangs typically attack the computer networks of businesses and other organizations, as the gangs can perform double extortion by exfiltrating company secrets or customer information and threatening to publish it. However, the addition of a ransomware module to an Android banking Trojan may be a sign that malicious actors see mobile devices as a ripe frontier for ransomware, particularly at a time when the median ransomware payment is declining in value. Mobile devices often contain users’ most sensitive information and function as users’ primary access point to all their online accounts and messaging services. A sizable portion of users locked out of their own phones by ransomware could be desperate enough to pay ransom fees.

Ransomware payments over time (source: Coveware)
Cybersecurity researchers at Cleafy have been watching the development of this banking Trojan for some time now. The malware was first announced in September 2021 and is known as SOVA. It targets over 200 mobile apps, including apps that give users access to banking, cryptocurrency exchanges and wallets, and other financial services. Beyond stealing financial information and login credentials, including two-factor-authentication (2FA) codes, from these apps, the malware has a wide array of capabilities. It can steal cookies, take screenshots, record activity, perform on-screen gestures to control infected devices, and display an overlay screen to hide what’s happening underneath from users. The malware is under active development, and the recently added ransomware module is still being improved.
Ransomware encrypts files on infected devices with encryption keys known only to the attacker, rendering the files inaccessible to the victims. The attacker then extorts the victims by asking them to pay ransom fees to have their data unencrypted. Ransomware gangs typically attack the computer networks of businesses and other organizations, as the gangs can perform double extortion by exfiltrating company secrets or customer information and threatening to publish it. However, the addition of a ransomware module to an Android banking Trojan may be a sign that malicious actors see mobile devices as a ripe frontier for ransomware, particularly at a time when the median ransomware payment is declining in value. Mobile devices often contain users’ most sensitive information and function as users’ primary access point to all their online accounts and messaging services. A sizable portion of users locked out of their own phones by ransomware could be desperate enough to pay ransom fees.