Apple Accidentally Approved Widespread Mac Malware Via App Security Notarization

Traditionally, Macs weren't often a target for malware campaigns given their relatively small share of the overall computing market. This notion has changed over the years, however, but Apple has fought back with increased security procedures like an app approval process called notarization. Unfortunately, malware has now been discovered in notarized code and is able to be executed as a normal program.
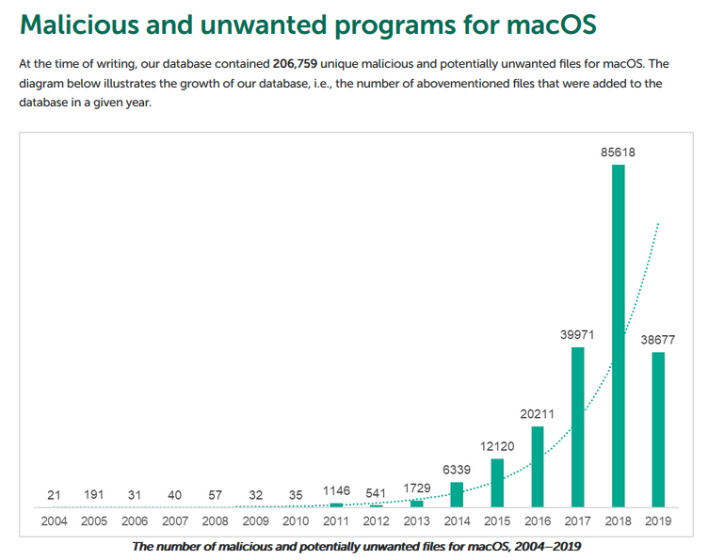
First off, an important note is that Macs can get malware, but it has to be specially designed. When Apple said that Macs cannot get malware, it was only true because of the specific design caveat. “Even back in 2012, thanks to Java, cross-platform malware could be found targeting both Windows and macOS”, Wardle states, “Today, malicious code targeting macOS, unfortunately, is far too common.” In his report, Wardle has a chart from Kapersky showing this.
This threat of malware to macOS is where notarization steps in. Apple wants to scan software for malware or “malicious content.” Malicious content would not be let through so Macs could not run it and install it. This notarization process would have, in theory, acted like a filter with no real flaws, until Peter Dantini shared some interesting information with Wardle.
On August 28th, Peter Dantini shared a website which hosted an “active adware campaign.” If a user went to the site, an update to “Adobe Flash Player” would be aggressively recommended and shown to the user. Peter then noticed that the payloads on site with the adware was notarized. When Wardle dug into the payloads a little more, he found that it was highly prevalent Shlayer adware hiding underneath.
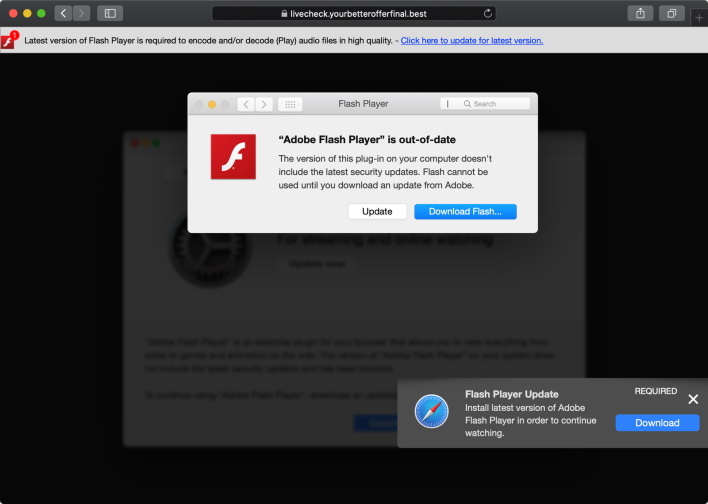
“Malicious software constantly changes, and Apple’s notarization system helps us keep malware off the Mac and allow us to respond quickly when it’s discovered. Upon learning of this adware, we revoked the identified variant, disabled the developer account, and revoked the associated certificates. We thank the researchers for their assistance in keeping our users safe.”
Apparently, the malicious code was re-notarized after Apple took down the original notarization. Of course, this probably will not be the last time this loop happens. The ingenuity of people creating malware knows no bounds. As Wardle puts it in the best way possible, it is a “never ending cat & mouse game between the attackers and Apple, the attackers are currently (still) winning.”

