Apple Plugs A Gaping Zero-Day Security Hole In iPhone And iPad, Install ASAP

At the top of September, The Citizen Lab was investigating the device of someone who worked in Washington, DC, at a “civil society organization with international offices.” In this investigation, the team found an actively exploited infection chain tied to the NSO Group’s Pegasus spyware. This exploit chain was dubbed BLASTPASS and was “capable of compromising iPhones running the latest version of iOS (16.6) without any interaction from the victim.”
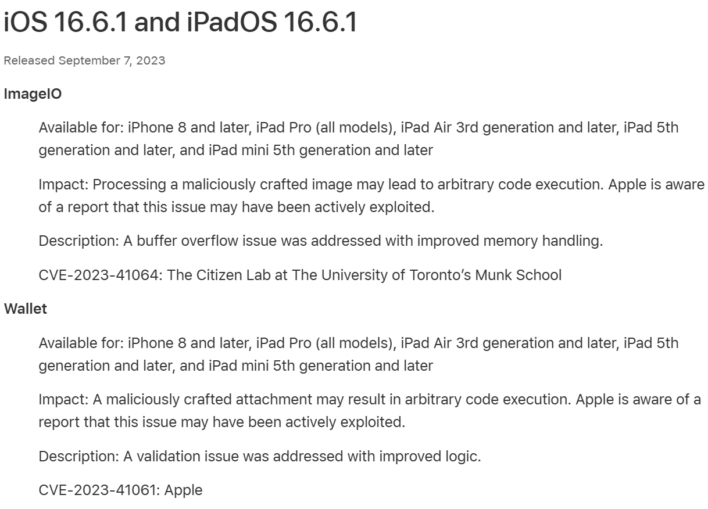
This infection chain was predicated on PassKit attachments with malicious images sent from a threat actor’s iMessage to the victim, who did not have to interact with the content, per The Citizen Lab report. Subsequently, the Lab sent its findings to Apple, whereupon two CVEs, or Common Vulnerabilities and Exposures, were generated: CVE-2023-41064 and CVE-2023-41061.
With this, Apple has pushed an update to iOS, iPadOS, watchOS, and MacOS that targets the vulnerabilities mentioned above within ImageIO and Wallet. Of course, it is highly recommended that Apple users update all their devices to this latest update to protect themselves from the infection chain. However, The Citizen Lab notes that “Apple’s Security Engineering and Architecture team has confirmed to [the Lab], that Lockdown Mode blocks this particular attack.”
For those unaware, Lockdown Mode is an option available in iOS 16, iPadOS 16, and macOS Ventura that reduces the attack surface of the device by disabling certain functions. Therefore, if you think you are at risk, it is worth enabling this setting as it seems to disrupt many of these zero-day, zero-click exploit chains for Apple.