Apple Moves Swiftly To Patch Privilege Escalation Exploit In OS X 10.10.5 Yosemite
The annual Black Hat convention in Las Vegas usually brings with it news of new vulnerabilities that sends manufacturers and software publishers scrambling to create patches. Announcements ahead of this year’s Black Hat are already causing headaches for one computer maker who rarely finds itself the target of major attacks: Apple.
Apple is taking steps to address two vulnerabilities for its Mac line of computers. As we mentioned earlier this week, researchers with security firm LegbaCore created a worm capable of storing itself in the ROM of peripherals and entering Macs via the Thunderbolt connection. The Thunderstrike 2 worm is capable of attacking a Mac’s firmware and can be difficult to detect once the system is infected.
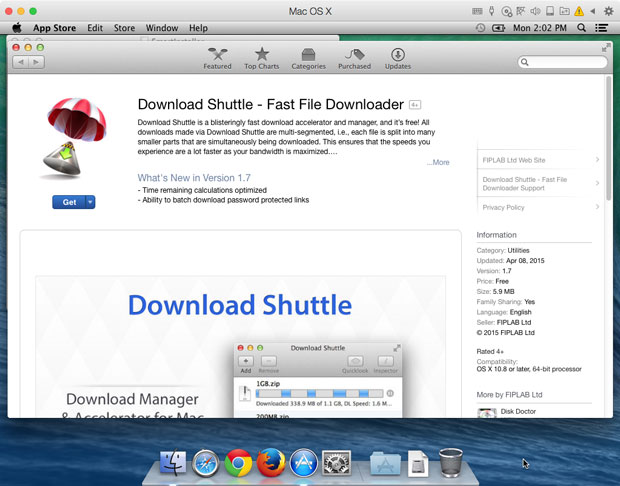
The other threat is actually a bug in Mac OS X 10.10.5. Known as DYLD, the vulnerability lets adware makers and other malicious users create software that can run as though the computer’s user had authorized it. A Malwarebytes recently discovered the first use of the exploit in the wild: malware that installs VSearch, as well as Genieo and MacKeeper. The exploit also opens a window to point users to Download Shuttle on the Mac App Store.
As scary as Thunderstrike 2 sounds, security experts appear to be less concerned by it (due largely to the expected difficulty the worm would have in spreading) than the DYLD bug. For one thing, the DYLD bug is already being exploited in the wild, whereas Thunderstrike 2 is a proof-of-concept worm.
Apple is working on fixes for both vulnerabilities and has already partially patched Thunderstrike 2 with Mac OS X 10.10.4. The DYLD bug will be addressed in the upcoming Mac OS X 10.10.5 update. Until the patch arrives, Apple is reportedly keeping an eye out for apps (on its store and elsewhere) that attempt to use the DYLD bug.
Apple is taking steps to address two vulnerabilities for its Mac line of computers. As we mentioned earlier this week, researchers with security firm LegbaCore created a worm capable of storing itself in the ROM of peripherals and entering Macs via the Thunderbolt connection. The Thunderstrike 2 worm is capable of attacking a Mac’s firmware and can be difficult to detect once the system is infected.
The other threat is actually a bug in Mac OS X 10.10.5. Known as DYLD, the vulnerability lets adware makers and other malicious users create software that can run as though the computer’s user had authorized it. A Malwarebytes recently discovered the first use of the exploit in the wild: malware that installs VSearch, as well as Genieo and MacKeeper. The exploit also opens a window to point users to Download Shuttle on the Mac App Store.
As scary as Thunderstrike 2 sounds, security experts appear to be less concerned by it (due largely to the expected difficulty the worm would have in spreading) than the DYLD bug. For one thing, the DYLD bug is already being exploited in the wild, whereas Thunderstrike 2 is a proof-of-concept worm.
Apple is working on fixes for both vulnerabilities and has already partially patched Thunderstrike 2 with Mac OS X 10.10.4. The DYLD bug will be addressed in the upcoming Mac OS X 10.10.5 update. Until the patch arrives, Apple is reportedly keeping an eye out for apps (on its store and elsewhere) that attempt to use the DYLD bug.