AvosLocker Ransomware Gang Mistakenly Hits Police Dept. And Backs Down But Why?

You may not be aware of this, faithful HotHardware reader, but ransomware attacks are rarely random. More commonly, it's an operator within a group who targets a specific organization or network looking for a hefty payout. One such group is the organization AvosLocker, who uses a tool by the same name to encrypt vulnerable systems and then charge the victims to get their data back.
Well, according to a screenshot shared on Twitter by @pancak3lullz (a known security researcher), an AvosLocker operator gave up their prey recently after finding out that their victim was a police department in the United States. The screenshot shows an AvosLocker chat message stating "Sorry on another note I've realized this is US gov, we will be allowing you to decrypt for free. Refresh for the decryptor."
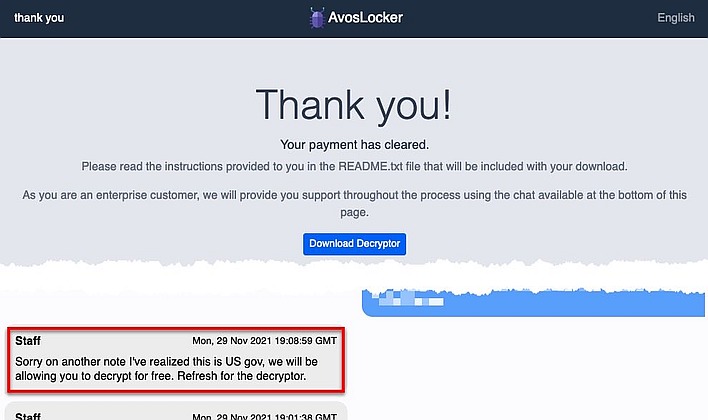
The ransomware operator went on to explain that while that's the case, "sometimes an affiliate will lock a network without having us review it first." Indeed, AvosLocker is one of numerous "ransomware as a service" operators. The group licenses its software to third-party operators who are the ones that then attack vulnerable targets. AvosLocker told BleepingComputer that it and its affiliates avoid targeting government agencies not out of fear, but simply because "tax payer money's generally hard to get."
Despite AvosLocker's cavalier attitude toward law enforcement—the group says it's not worried about police because they "have no jurisdiction in the motherland"—international law enforcement has been making great strides in shuttting down ransomware operations. As just a few examples, members of the Egregor and Netwalker ransomware operations are in custody, while the REvil and Avaddon networks have apparently been completely shut down.

