China's Long-Term, Low-Budget Hacks Of Human Rights Groups Are Infuriating

Threat intelligence firm Recorded Future has published a report concerning a long-term credential theft campaign targeting humanitarian, think tank, and government organizations. A hacking group known as RedAlpha is carrying out this ongoing campaign, and is known to have been active as far back as 2015. However, it wasn’t until 2018 that the group was first identified. RedAlpha is believed to be a group of threat actors contracted by the Chinese government to perform cyber-espionage at its behest, as the group has ties to personas and a private company located within China.
RedAlpha targets humanitarian and human rights organizations that seek to uncover and end China’s human rights abuses against the Uyghurs, Tibetans, and other ethnic and religious minority groups in China. The group has also more recently expanded its scope to target political, government, and think tank organizations in the democratic country of Taiwan. The Chinese Communist Party (CCP) denies Taiwan’s claim to independence and may be preparing to forcibly subsume the small country under its rule. RedAlpha may be assisting in this preparation by gathering intelligence through cyber-espionage.
RedAlpha targets humanitarian and human rights organizations that seek to uncover and end China’s human rights abuses against the Uyghurs, Tibetans, and other ethnic and religious minority groups in China. The group has also more recently expanded its scope to target political, government, and think tank organizations in the democratic country of Taiwan. The Chinese Communist Party (CCP) denies Taiwan’s claim to independence and may be preparing to forcibly subsume the small country under its rule. RedAlpha may be assisting in this preparation by gathering intelligence through cyber-espionage.
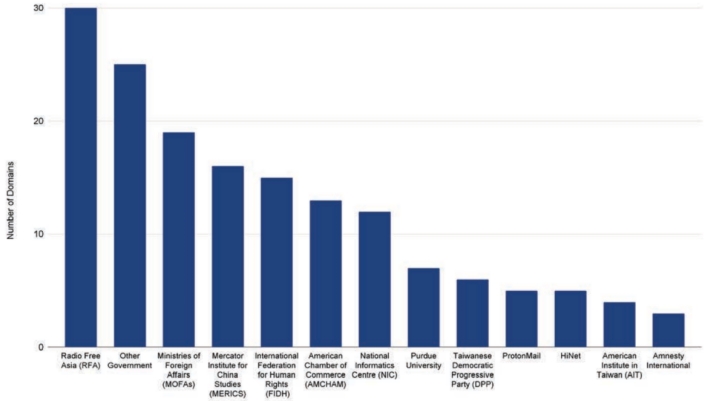
RedAlpha’s continued credential theft campaign employs phishing techniques intended to trick unsuspecting members of target organizations from giving away user credentials. The threat actors look to be conducting homograph attacks in which the attackers register domains that appear similar to legitimate domains used by the target organizations but have typos, extra characters, or non-Latin characters. Recorded Future found that RedAlpha registered a total of 350 domains in 2021 for this purpose.
In many cases, visitors to these domains found login portals mimicking those of the specific organizations being targeted. Anyone who fell for these imitations and entered their login credentials risked granting RedAlpha unauthorized access to their organizations’ online systems. While this credential theft campaign is clearly malicious and reprehensible, it’s a lower budget and less sophisticated cyber-espionage effort than we’ve seen from other Chinese state-sponsored hackers.
We’ve reported this year on more widespread cyber-espionage campaigns that rely on malware and vulnerability exploits to steal intellectual property, snoop on network traffic, and install backdoors in target systems. Researching vulnerabilities, developing exploits, and deploying malware in a targeted manner can be more labor intensive than registering domains and copying login portals. However, this comparison doesn’t make RedAlpha’s campaign any less sinister.
In many cases, visitors to these domains found login portals mimicking those of the specific organizations being targeted. Anyone who fell for these imitations and entered their login credentials risked granting RedAlpha unauthorized access to their organizations’ online systems. While this credential theft campaign is clearly malicious and reprehensible, it’s a lower budget and less sophisticated cyber-espionage effort than we’ve seen from other Chinese state-sponsored hackers.
We’ve reported this year on more widespread cyber-espionage campaigns that rely on malware and vulnerability exploits to steal intellectual property, snoop on network traffic, and install backdoors in target systems. Researching vulnerabilities, developing exploits, and deploying malware in a targeted manner can be more labor intensive than registering domains and copying login portals. However, this comparison doesn’t make RedAlpha’s campaign any less sinister.

