CISA Warns Of Heightened Hacking Threat Using Legit Remote Desktop Tools

Yesterday, the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) published a joint cybersecurity advisory warning network defenders about phishing attacks that leverage remote monitoring and management (RMM) software. This advisory comes after CISA discovered malicious RMM activity on two federal civilian executive branch (FCEB) networks and identified this activity as part of a larger refund scam campaign.
RMM software, similar to remote desktop software, provides users with a set of tools to remotely access and manage computer systems. Unfortunately, as we reported recently, threat actors have taken to using this legitimate software in place of malware to access victims’ devices. Since RMM software is also used by those providing authentic IT support, it can be difficult for users to distinguish between legitimate and malicious uses of this software, particularly when threat actors pose as IT support technicians.
RMM software, similar to remote desktop software, provides users with a set of tools to remotely access and manage computer systems. Unfortunately, as we reported recently, threat actors have taken to using this legitimate software in place of malware to access victims’ devices. Since RMM software is also used by those providing authentic IT support, it can be difficult for users to distinguish between legitimate and malicious uses of this software, particularly when threat actors pose as IT support technicians.
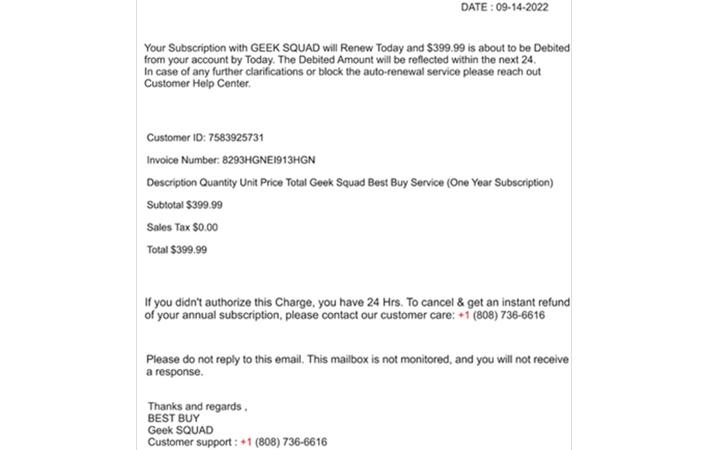
Starting in June 2022, FCEB staff began receiving phishing emails listing fake, unexpected invoices. Some of these emails prompted recipients to directly visit fraudulent support websites, while others directed recipients to call customer care phone numbers. Calls to these numbers were answered by phony customer support agents who pointed callers to the same fraudulent support websites as the ones linked in other phishing emails.
These websites served RMM software executables to visitors under the pretense that customer support agents would use the software to help resolve problems with the invoice refund process. Since portable executables skip the installation process and directly launch programs, the RMM software distributed by the threat actors could bypass security controls blocking the installation of unapproved programs. The RMM software, whether AnyDesk or ScreenConnect, was configured to automatically connect to the threat actor’s RMM servers, giving the threat actors access to victims’ computers shortly after launching.
Once the RMM software was running, the threat actors continued to pose as customer support agents, requesting that victims log into their bank accounts in their web browsers to check for money refunded from the fake invoices. The threat actors then leveraged their access to victims’ systems to modify bank interfaces to display refunds in excess of the expected amount. Lastly, the phony customer support agents explained these over-value refunds as mistakes and guided victims through the process of “returning” the excess money.
The cybersecurity advisory warns that, while this particular phishing campaign seems financially motivated, any persistent unauthorized access established by the threat actors could later be leveraged for more nefarious ends. Recommended mitigation measures include auditing remote access tools on relevant networks and reviewing logs to check for any unauthorized activity. The advisory lists indicators of compromise (IOCs), which organizations can use to check for activity associated with the particular phishing campaign highlighted in the notice.
These websites served RMM software executables to visitors under the pretense that customer support agents would use the software to help resolve problems with the invoice refund process. Since portable executables skip the installation process and directly launch programs, the RMM software distributed by the threat actors could bypass security controls blocking the installation of unapproved programs. The RMM software, whether AnyDesk or ScreenConnect, was configured to automatically connect to the threat actor’s RMM servers, giving the threat actors access to victims’ computers shortly after launching.
Once the RMM software was running, the threat actors continued to pose as customer support agents, requesting that victims log into their bank accounts in their web browsers to check for money refunded from the fake invoices. The threat actors then leveraged their access to victims’ systems to modify bank interfaces to display refunds in excess of the expected amount. Lastly, the phony customer support agents explained these over-value refunds as mistakes and guided victims through the process of “returning” the excess money.
The cybersecurity advisory warns that, while this particular phishing campaign seems financially motivated, any persistent unauthorized access established by the threat actors could later be leveraged for more nefarious ends. Recommended mitigation measures include auditing remote access tools on relevant networks and reviewing logs to check for any unauthorized activity. The advisory lists indicators of compromise (IOCs), which organizations can use to check for activity associated with the particular phishing campaign highlighted in the notice.