Cloud9 Botnet Employs Malicious Extensions To Take Control Of Browsers and Windows
Researchers at the cybersecurity firm Zimperium have discovered a botnet made up of web browsers infected by malware. The malware in question is known as Cloud9 and takes the form of browser extensions. When installed, these browser extensions take control of infected browsers to steal valuable information and perform DDoS attacks. The malware within these extensions is also capable of leveraging various vulnerabilities to escape the browser and infect the Windows operating system.
Unlike other malicious browser extensions, the extensions containing the Cloud9 malware have never been available on any official browser extension stores, as far as Zimperium is aware. Threat actors instead seem to spread the malware most commonly on websites offering fake Adobe Flash Player updates. While Adobe officially discontinued Flash Player in December 2020 and most modern web browsers don’t support Flash, some websites still offer Flash games and other web content. Some users may be driven to websites that promote Flash Player updates in the hopes of accessing this content.
Unlike other malicious browser extensions, the extensions containing the Cloud9 malware have never been available on any official browser extension stores, as far as Zimperium is aware. Threat actors instead seem to spread the malware most commonly on websites offering fake Adobe Flash Player updates. While Adobe officially discontinued Flash Player in December 2020 and most modern web browsers don’t support Flash, some websites still offer Flash games and other web content. Some users may be driven to websites that promote Flash Player updates in the hopes of accessing this content.
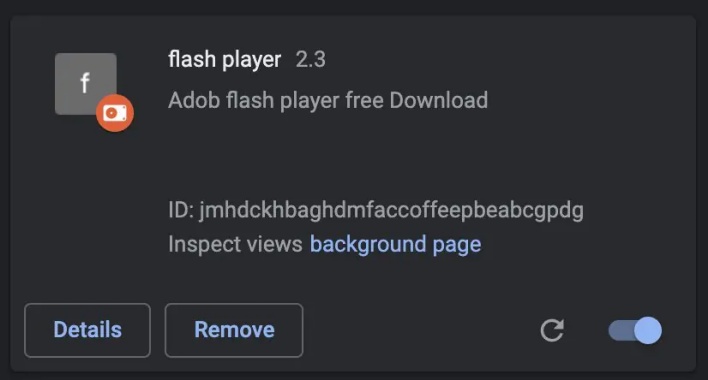
Unfortunately, threat actors are all too willing to take advantage of such users by providing them with malware-laden browser extensions disguised as Adobe Flash Player. The Cloud9 malware contained within these extensions possesses a wide array of abilities, including cookie-stealing and keylogging. Beyond pilfering login sessions and any information entered into text fields, Cloud9 can mine cryptocurrency within infected browsers and direct the browsers to perform distributed denial-of-service (DDoS) attacks, like those recently directed at the Overwatch 2 and Wynncraft servers.
As if malicious behavior inside infected browsers isn’t enough, Cloud9 can also break out of the browser to infect the operating system (OS). The malware begins by identifying a machine’s operating system and browser, then reaching out to a command-and-control (C2) server to download additional malicious payloads for further attacks. If the infected browser is Firefox, Microsoft Edge, or Internet Explorer and the underlying OS is Windows, Cloud9 can leverage different exploits to escape the browser.
The vulnerabilities in question are relatively old, dating from 2014 to 2019, and have since been patched. Nonetheless, four out of five of them appeared on the Cybersecurity and Infrastructure Agency’s (CISA) Known Exploited Vulnerabilities Catalog in 2022, meaning threat actors are still exploiting these vulnerabilities because some machines are still running old versions of the affected web browsers. In order to avoid falling prey to the Cloud9 malware, users and organizations should make sure to install the latest security updates and refrain from installing browser extensions claiming to be Adobe Flash Player.
As if malicious behavior inside infected browsers isn’t enough, Cloud9 can also break out of the browser to infect the operating system (OS). The malware begins by identifying a machine’s operating system and browser, then reaching out to a command-and-control (C2) server to download additional malicious payloads for further attacks. If the infected browser is Firefox, Microsoft Edge, or Internet Explorer and the underlying OS is Windows, Cloud9 can leverage different exploits to escape the browser.
The vulnerabilities in question are relatively old, dating from 2014 to 2019, and have since been patched. Nonetheless, four out of five of them appeared on the Cybersecurity and Infrastructure Agency’s (CISA) Known Exploited Vulnerabilities Catalog in 2022, meaning threat actors are still exploiting these vulnerabilities because some machines are still running old versions of the affected web browsers. In order to avoid falling prey to the Cloud9 malware, users and organizations should make sure to install the latest security updates and refrain from installing browser extensions claiming to be Adobe Flash Player.

