Cloudflare Details How It Thwarted The Same Smishing Attack That Stung Twilio

Cloudflare says that it was hit by the same smishing (sms phishing) attack that recently resulted in a user data breach at Twilio. However, unlike Twilio, Cloudflare managed to prevent the attack from escalating to a data breach thanks to its strong security measures. While the attackers managed to steal login credentials from Cloudflare employees, they were unable to use any of these credentials to access Cloudflare’s internal systems because the company’s employees are required to use physical security keys during the login process. As the attackers did not have access to those physical security keys, the stolen login credentials were rendered useless.
This attack mirrored the smishing attack suffered by Twilio, which does not come as a surprise since Twilio hinted that other companies were hit by the same attack. Cloudflare’s blog post recounting the attack includes additional details that reveal how sophisticated and fast moving the attack was. Cloudflare employees are trained to report suspicious messages and behavior to the company’s Security Incident Response Team, and Twilio employees are likely trained to file similar reports. As a result, the attackers have to move quickly in order to be successful.
This attack mirrored the smishing attack suffered by Twilio, which does not come as a surprise since Twilio hinted that other companies were hit by the same attack. Cloudflare’s blog post recounting the attack includes additional details that reveal how sophisticated and fast moving the attack was. Cloudflare employees are trained to report suspicious messages and behavior to the company’s Security Incident Response Team, and Twilio employees are likely trained to file similar reports. As a result, the attackers have to move quickly in order to be successful.
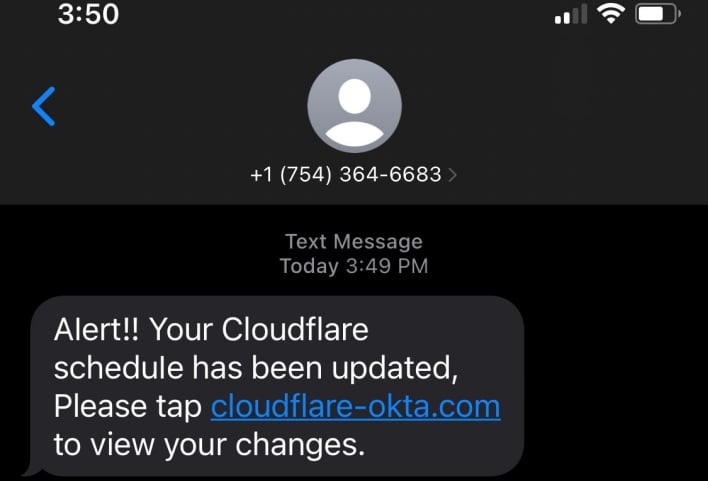
Just like the attack on Twilio, the attack on Cloudflare started with SMS messages sent to Cloudflare employees. Using just four phone numbers on the T-Mobile network, the threat actors sent fraudulent messages to at least 76 employees in under a minute. Some employees’ family members also received fraudulent messages. These targeted messages reveal the threat actors’ ability to independently match employee names and phone numbers, as Cloudflare’s own directory services show no sign of compromise.
The fraudulent messages directed their recipients to visit the domain cloudflare-okta.com. Some employees took this to be a legitimate Cloudflare domain, since the company uses Okta as its identity provider. The threat actors registered this domain less than 40 minutes before sending the fraudulent SMS messages. Registering the domain this shortly beforehand also speaks to the speed and sophistication of the attack. Cloudflare runs an automated system that detects newly registered domains using the Cloudflare brand name so the company can shut them down. However, the threat actors registered their domain so soon before the attack that the domain was not yet published as a new registration at the time of the attack. As a result, Cloudflare’s automated system hadn’t yet alerted the company of the fraudulent domain’s registration.
The fraudulent messages directed their recipients to visit the domain cloudflare-okta.com. Some employees took this to be a legitimate Cloudflare domain, since the company uses Okta as its identity provider. The threat actors registered this domain less than 40 minutes before sending the fraudulent SMS messages. Registering the domain this shortly beforehand also speaks to the speed and sophistication of the attack. Cloudflare runs an automated system that detects newly registered domains using the Cloudflare brand name so the company can shut them down. However, the threat actors registered their domain so soon before the attack that the domain was not yet published as a new registration at the time of the attack. As a result, Cloudflare’s automated system hadn’t yet alerted the company of the fraudulent domain’s registration.
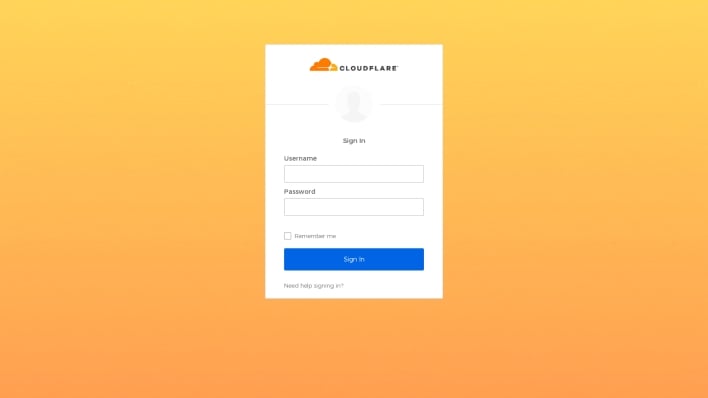
Those who visited the domain controlled by the threat actors found a login page that mimicked Cloudflare’s legitimate Okta login page. Some of the company’s employees did not realize that this login page was controlled by malicious attackers and entered their login credentials. These credentials were immediately sent to the threat actors over Telegram, who then entered them into Cloudlare’s actual login page. Meanwhile, the fraudulent login page asked the company’s employees to enter a Time-based One Time Password (TOTP). This is the point at which the attack failed, as Cloudflare uses physical security keys for two-factor authentication (2FA), rather than TOTPs.
That said, the threat actors were able to gain unauthorized access to Twilio’s internal systems, so presumably Twilio does use TOTPs for 2FA, and some of its employees entered TOTPs when prompted to do so. These codes were then sent to the attackers via Telegram, and subsequently entered into Twilio’s actual login page, defeating Twilio’s 2FA security measure. The fact that Cloudflare was able to thwart this smishing attack, while Twilio was not, demonstrates how hardware security keys can prevent remote cyberattacks from succeeding. Cloudflare attests to this takeaway in its blog post, stating that the company hasn’t experienced any successful phishing attacks since implementing physical security keys.
That said, the threat actors were able to gain unauthorized access to Twilio’s internal systems, so presumably Twilio does use TOTPs for 2FA, and some of its employees entered TOTPs when prompted to do so. These codes were then sent to the attackers via Telegram, and subsequently entered into Twilio’s actual login page, defeating Twilio’s 2FA security measure. The fact that Cloudflare was able to thwart this smishing attack, while Twilio was not, demonstrates how hardware security keys can prevent remote cyberattacks from succeeding. Cloudflare attests to this takeaway in its blog post, stating that the company hasn’t experienced any successful phishing attacks since implementing physical security keys.

