Conti Ransomware Campaign Blitz Hits Over 40 Companies In 5 Weeks

Shortly after hitting Parker Hannifin Corporation, a major component supplier for Boeing and Lockheed Martin, the Conti ransomware group abandoned the Conti name and split off into smaller groups that coordinate with the larger group’s leadership. This move came after Conti targeted the government of Costa Rica with ransomware. By targeting a government, the ransomware group may have invoked state actors to increase their efforts to take down Conti leadership, forcing the group to break apart into smaller cells for increased operations security (OPSEC). Even before the attack on Costa Rica’s government, the US Department of State announced a $10 million reward for information that helps identify or locate key members of the Conti ransomware group.
While Conti may no longer be operating under that name, cybersecurity researchers are still analyzing attacks perpetrated by the group before its dissolution. Researchers at the cybersecurity firm Group-IB have published a report detailing a particular ransomware campaign carried out by Conti between November 17 and December 20, 2021. According to Group-IB, the campaign, codenamed “ARMattack,” was one of the ransomware groups’ quickest and most productive campaigns.
While Conti may no longer be operating under that name, cybersecurity researchers are still analyzing attacks perpetrated by the group before its dissolution. Researchers at the cybersecurity firm Group-IB have published a report detailing a particular ransomware campaign carried out by Conti between November 17 and December 20, 2021. According to Group-IB, the campaign, codenamed “ARMattack,” was one of the ransomware groups’ quickest and most productive campaigns.
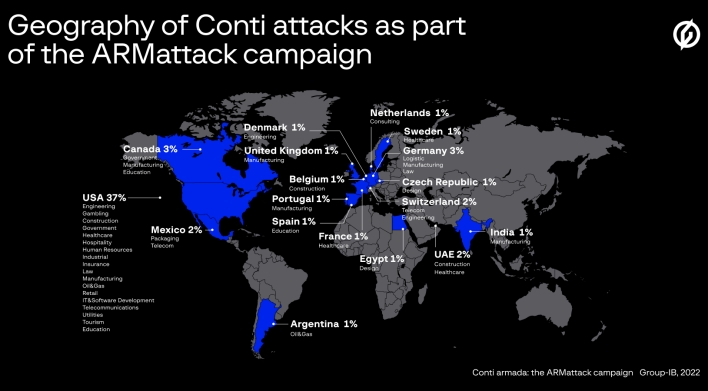
In a little under five weeks, the Conti ransomware gang compromised the computer systems of over 40 companies across the world, with the plurality being located in the US. Thanks to actors in different time zones, Conti was able to operate 14 hours out of the day during this campaign and completed one attack in just three days. Once the group successfully gained unauthorized access to a network, it would exfiltrate key documents, including files containing passwords, then perform privilege escalation and gain access to all desired devices. Lastly, the group would deploy ransomware to all compromised devices, encrypting the data within, and publicize the attack on the group’s dedicated leak site, threatening to publicly release the encrypted data if the ransom wasn’t paid.
It’s worth nothing that the ARMattack campaign didn’t hit a single company located in Russia. Conti is a Russian-speaking organization and, beyond the unspoken rule that Russian cybercriminals don’t attack Russian companies, the ransomware group has made public statements declaring its allegiance to Russia and its government. When Russia began its invasion of Ukraine, the Conti ransomware gang announced its full support of the Russian government and threatened to conduct counterattacks against anyone who carried out cyberattacks or other offensive measures against Russia.
It’s worth nothing that the ARMattack campaign didn’t hit a single company located in Russia. Conti is a Russian-speaking organization and, beyond the unspoken rule that Russian cybercriminals don’t attack Russian companies, the ransomware group has made public statements declaring its allegiance to Russia and its government. When Russia began its invasion of Ukraine, the Conti ransomware gang announced its full support of the Russian government and threatened to conduct counterattacks against anyone who carried out cyberattacks or other offensive measures against Russia.

