Dell SupportAssist Exposed 30 Million PCs To Potential Remote BIOS Hack, Update Now

Security researchers have sounded the alarm on four BIOS vulnerabilities affecting 129 different Dell models, including various laptop and desktop systems, as well as some tablets. In total, it is estimated that around 30 million Dell systems are susceptible to the vulnerabilities and should be patched right away. Fortunately, Dell has issued updates for all affected models.
If left unpatched, an attacker could execute malicious code without having physical access to a system, and it would run in the pre-boot environment. This is how rootkits normally operate—they corrupt the BIOS, so if a user wipes their system clean with a fresh OS install, or even swaps out the physical drive (SSD or HDD), the malicious code persists.
"Such code may alter the initial state of an operating system, violating common assumptions on the hardware/firmware layers and breaking OS-level security controls. As attackers increasingly shift their focus to vendor supply chains and system firmware, it is more important than ever that organizations have independent visibility and control over the integrity of their devices," security researchers at Eclypsium stated in a blog post.
Ironically enough, the vulnerabilities were introduced through Dell's SupportAssist software, which is supposed to help keep systems up to date and avoid these very kinds of issues. SupportAssist comes preinstalled on many of Dell's PCs, and includes a range of functions, like hardware monitoring, troubleshooting, and so forth.
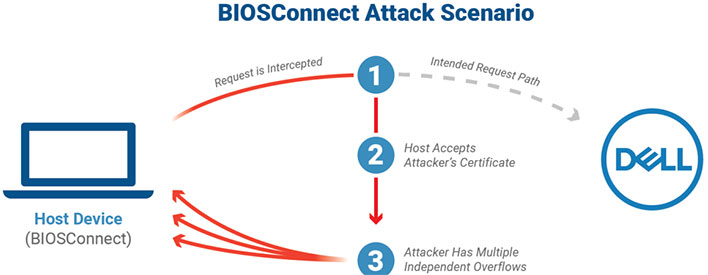
One of the features of the utility is BIOSConnect. This enables users to perform BIOS updates and recover their OS remotely.
"Our research has identified a series of four vulnerabilities that would enable a privileged network attacker to gain arbitrary code execution within the BIOS of vulnerable machines. The vulnerabilities were originally discovered on a Dell Secured-core PC Latitude 5310 using Secure Boot, and we later confirmed the issue on other models of desktops and laptops," the researchers said.
The four flaws include an issue that could lead to an insecure TLS connection from the BIOS to Dell's servers (CVE-2021-21751), and a trio of overflow vulnerabilities (CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574). The chain of vulnerabilities carry a cumulative CVSS score of 8.3 (High) because they potentially enable a privileged network adversary to impersonate a Dell server and then run malicious code at BIOS/UEFI level on an affected machine.
"Successfully compromising the BIOS of a device would give an attacker a high degree of control over a device. The attacker could control the process of loading the host operating system and disable protections in order to remain undetected. This would allow an attacker to establish ongoing persistence while controlling the highest privileges on the device," the researchers added.
The researchers have been working with Dell on the matter, which posted a security advisory saying it has released remediations for the issues at hand. As part of the advisory, Dell posted a long list of affected models, some of which include the Alienware m15 R6 and a whole bunch of G-series, Inspiron, Precision, Vostro, and XPS systems.
BIOS updates are available for all affected systems, and according to Dell, they fully address the aforementioned vulnerabilities.