Dexphot Malware Enslaved Nearly 80,000 Computers To Mine Cryptocurrency

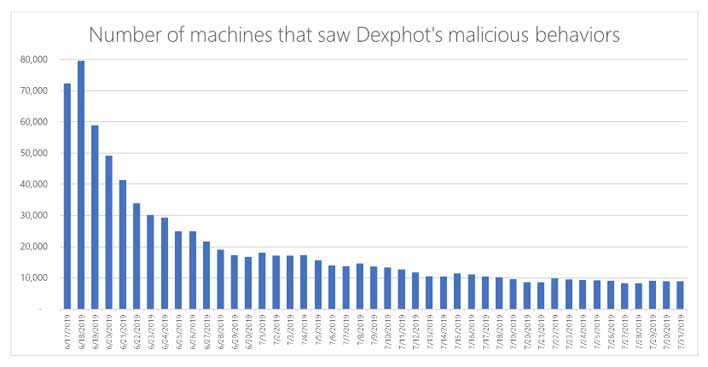
Dexphot reached its peak in mid-June of 2019 when the botnet had reached nearly 80,000 infected computers. The botnet has shrunk since then as Microsoft has rolled out countermeasures to improve detection and stop attacks. What stood out about Dexphot was the high level of complexity that the attack employed in its methods and techniques.
Dexphot used advanced techniques such as fileless execution, polymorphic techniques, and smart and redundant boot persistence mechanisms. Dexphot was taking advantage of computers that were previously infected with ICLoader; a malware strain usually side-installed as part of a software bundle without the user knowing. It was often installed when users downloaded and installed cracked or pirated software.
On some of the ICLoader-infected systems, the ICLoager gang was downloading and running the Dexphot installer. Microsoft says that the installer would be the only part of the malware written to disk and only for a short period. All the other files needed for the malware ran in the computer memory only, making it invisible to some signature-based AV solutions.
Dexphot also used something called LOLbins to abuse legitimate Windows processes to execute malicious code and polymorphism, a malware technique where it continuously changes its artifacts. Microsoft says that operators of the malware changed filenames and URLs used in the infection process every 20-30 minutes.
The techniques in the malware were so complicated that it says you usually expect this sort of redundancy to be found in malware developed by advanced government-backed hacking units. These techniques are slowly ending up in the hands of cyber-criminal gangs.

