Facebook and Instagram's In-App Browser Exploits Expose User Privacy Concerns

Facebook’s collection and sale of user data for advertising purposes took a huge hit when Apple introduced its App Tracking Transparency (ATT) feature, with Facebook projecting that it will lose out on $10 billion in revenue this year. However, it appears that Meta, Facebook’s parent company, may still have some behavior tracking tricks up its sleeve. New research shows that the Facebook, Instagram, and Messenger mobile apps inject a custom script through their in-app browsers.
Some mobile apps open links in an in-app browser, rather than opening them in the user's default browser app. In the case of iOS, the default browser app is Apple’s own Safari web browser, unless users change this in the device settings. When app developers want their users to briefly view websites without jumping over to the Safari app, Apple recommends that developers use SFSafariViewController, which opens a restricted Safari viewport. Nonetheless, Apple doesn’t prohibit app developers from building their own web browsers into their apps, though the company does discourage the use of this technique.
Some mobile apps open links in an in-app browser, rather than opening them in the user's default browser app. In the case of iOS, the default browser app is Apple’s own Safari web browser, unless users change this in the device settings. When app developers want their users to briefly view websites without jumping over to the Safari app, Apple recommends that developers use SFSafariViewController, which opens a restricted Safari viewport. Nonetheless, Apple doesn’t prohibit app developers from building their own web browsers into their apps, though the company does discourage the use of this technique.
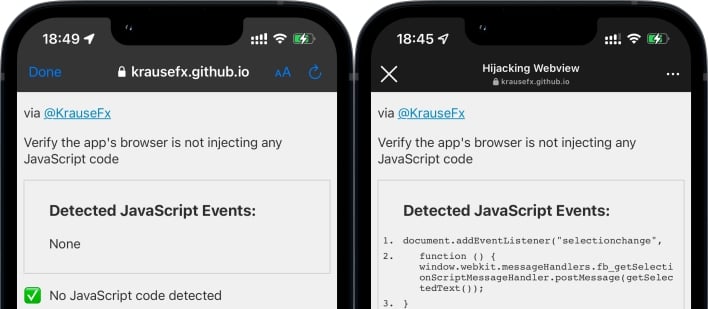
Meta takes advantage of this allowance by building custom web browsers into its Facebook, Instagram, and Messenger mobile apps that inject JavaScript into web pages. A researcher by the name of Felix Krause built a tool to detect JavaScript injection and opened this tool in various mobile apps. As expected, apps that use Apple’s SFSafariViewController, like Telegram, don’t inject any JavaScript. However, Krause’s tool detected JavaScript injection when opened in the custom web browsers built into the Facebook, Instagram, and Messenger mobile apps.
At first, Krause thought that these custom in-app browsers might be injecting the Meta Pixel, which is a bit of JavaScript code that tracks user behavior across websites. However, Meta reached out to the researcher through email to clarify that the injected JavaScript code is not the Meta Pixel, but rather a script named pcm.js. The pcm.js code includes comments that discuss scraping documents for image scripts and tagging them with a tracking url, but we can’t decipher what all the code does. According to Meta, this script helps the in-app browsers respect users’ App Tracking Transparency settings in the case that visited websites contain the Meta Pixel.
Regardless of what this particular script does, this research raises broader privacy and security concerns. The Facebook, Instagram, and Messenger apps demonstrate that it is possible for apps to come packaged with their own web browsers that inject custom JavaScript into web pages. App developers looking to collect information about their users’ behavior on the websites they visit could inject JavaScript that would do just that. A possibly more sinister application for this technique could be a malicious app with a built-in web browser that injects code to steal login credentials or other sensitive information users enter into web forms.
Fortunately, most in-app browsers can be avoided with an option that will let users open webpages in the default browser. In the case that this option isn’t offered, users may want to manually copy links and paste them into their web browser of choice.
At first, Krause thought that these custom in-app browsers might be injecting the Meta Pixel, which is a bit of JavaScript code that tracks user behavior across websites. However, Meta reached out to the researcher through email to clarify that the injected JavaScript code is not the Meta Pixel, but rather a script named pcm.js. The pcm.js code includes comments that discuss scraping documents for image scripts and tagging them with a tracking url, but we can’t decipher what all the code does. According to Meta, this script helps the in-app browsers respect users’ App Tracking Transparency settings in the case that visited websites contain the Meta Pixel.
Regardless of what this particular script does, this research raises broader privacy and security concerns. The Facebook, Instagram, and Messenger apps demonstrate that it is possible for apps to come packaged with their own web browsers that inject custom JavaScript into web pages. App developers looking to collect information about their users’ behavior on the websites they visit could inject JavaScript that would do just that. A possibly more sinister application for this technique could be a malicious app with a built-in web browser that injects code to steal login credentials or other sensitive information users enter into web forms.
Fortunately, most in-app browsers can be avoided with an option that will let users open webpages in the default browser. In the case that this option isn’t offered, users may want to manually copy links and paste them into their web browser of choice.

