FBI Beats Hive Ransomware Gang At Its Own Hacking Game With A $10M Bounty

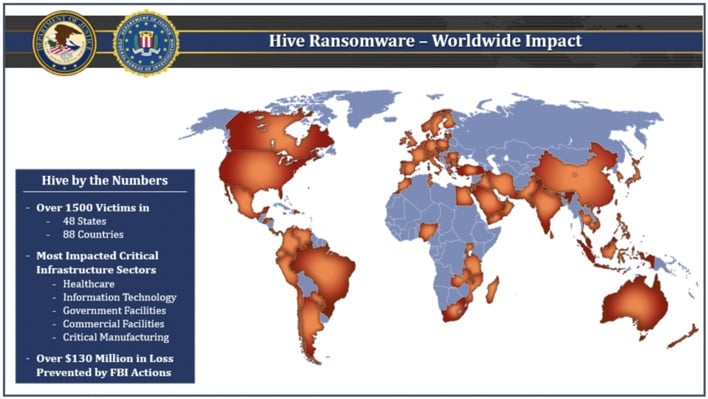
Last November, two weeks after the Biden administration held the second International Counter Ransomware Summit, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) published a joint cybersecurity advisory warning organizations about the threat posed by the Hive ransomware gang. At that time, the FBI counted over 1,300 organizations as victims of the threat group, costing these organizations a combined $100 million in ransom fees. However, what we didn’t know then was that the FBI had infiltrated Hive’s internal network in July 2022 and had since been counteracting the gang’s attacks by providing decryption keys to its victims. Fast forward to this week, and the FBI has now seized the servers and websites that Hive used to run its criminal operation.
Like most ransomware, Hive ransomware encrypted victims’ files with decryption keys known only to the attackers. The gang then attempted to extort victims by offering to hand over the decryption keys if victims paid ransom fees. According to the US Department of Justice (DoJ), by infiltrating Hive’s network, the FBI was able to provide over 1,300 decryption keys to victims of Hive ransomware. The FBI estimates that its distribution of these keys saved victims over $130 million in ransom fees.
Like most ransomware, Hive ransomware encrypted victims’ files with decryption keys known only to the attackers. The gang then attempted to extort victims by offering to hand over the decryption keys if victims paid ransom fees. According to the US Department of Justice (DoJ), by infiltrating Hive’s network, the FBI was able to provide over 1,300 decryption keys to victims of Hive ransomware. The FBI estimates that its distribution of these keys saved victims over $130 million in ransom fees.
Nonetheless, data encryption was only one half of Hive’s extortion strategy. The gang conducted doubled extortion by not only encrypting victims’ files, but first exfiltrating copies of the unencrypted files and later threatening to publish them to its dedicated leak site (DLS). Sadly, helping victims recover their encrypted files by providing decryption keys did nothing to mitigate this second and potentially more damaging half of the extortion threat.
Fortunately, the FBI’s efforts to thwart Hive’s cybercriminal activity didn’t end with its intrusion into the gang’s network. With the assistance of many US and international law enforcement agencies, the FBI was able to locate and seize the servers that ran not only Hive’s DLS, but also the gang’s management and communication infrastructure. According to the affidavit filed shortly before the seizure, the servers were located in a California data center and leased by three email addresses determined to be associated with the Hive operators.
Fortunately, the FBI’s efforts to thwart Hive’s cybercriminal activity didn’t end with its intrusion into the gang’s network. With the assistance of many US and international law enforcement agencies, the FBI was able to locate and seize the servers that ran not only Hive’s DLS, but also the gang’s management and communication infrastructure. According to the affidavit filed shortly before the seizure, the servers were located in a California data center and leased by three email addresses determined to be associated with the Hive operators.

While the FBI may have shut down and commandeered Hive’s server infrastructure and helped the gang’s victims recover their encrypted data, as far as we know, no arrests were made as part of this counter-ransomware operation. With Hive’s developers and affiliates still at large, it’s not at all unlikely that these cybercriminals will return under a new name or join other ransomware gangs.
Law enforcement agencies are still attempting to determine the identities and locations of these threat actors, with the US government is offering up to $10 million in exchange for information concerning cybercriminals. Shortly after the DoJ announced the FBI’s seizure of Hive’s servers, the US Department of State’s Rewards for Justice Program tweeted, “If you have information that links Hive or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government, send us your tip via our Tor tip line. You could be eligible for a reward.”
Law enforcement agencies are still attempting to determine the identities and locations of these threat actors, with the US government is offering up to $10 million in exchange for information concerning cybercriminals. Shortly after the DoJ announced the FBI’s seizure of Hive’s servers, the US Department of State’s Rewards for Justice Program tweeted, “If you have information that links Hive or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government, send us your tip via our Tor tip line. You could be eligible for a reward.”

