How To Use Open Source Intelligence To Help Secure Your Digital Footprint

Google Dorks & Search Engines

Leading off the lineup, the easiest means by which one can find themselves is by using search engines effectively. Of course, you can always search for your name and see what comes up, but that might be challenging if there are multiple people with the same name or if there is just a lot of content relating to you. Enter Google Dorks or otherwise known as “dorking”: a means by which you can craft specialized search queries to narrow down what results come back making search easier.
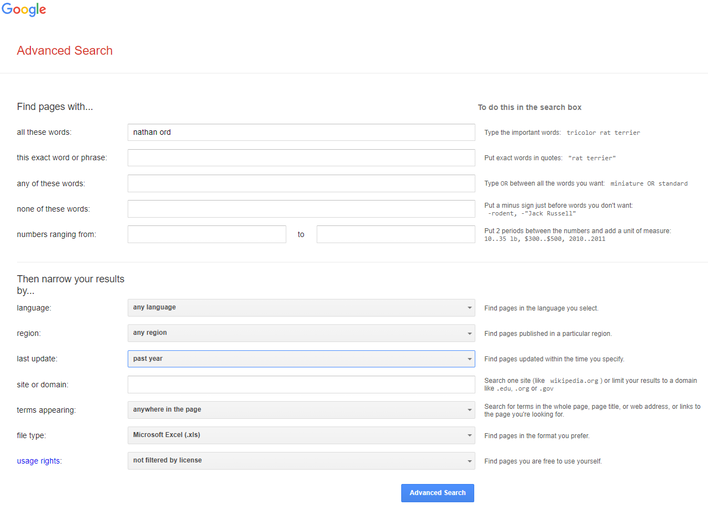
The first resource you can use relating to this is Google’s own Advanced Search feature of Google which can help you specify search terms, regions, file types, and much more. With this, for example, you could search for your name or email and a file type of xls updated in the past year to see if a spreadsheet somewhere online contains your name or email and is publicly accessible. However, Google’s Advanced Search does not quite cover all the possibilities here, so we will point toward ExploitDB’s list of Google Dorks dubbed the Google Hacking Database. This list contains thousands of different Google Dorks that you can use, customize, or tailor for your needs.
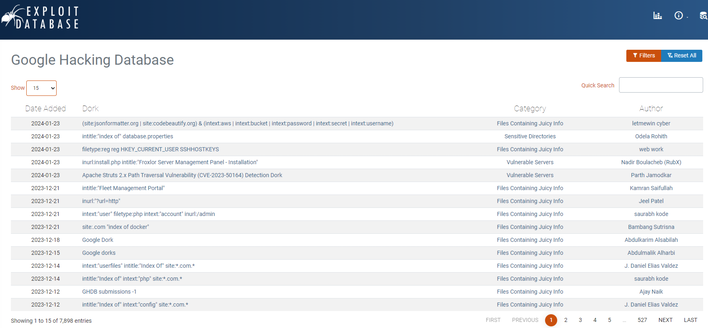
Google Dorks is one of those things that is not thought about too often but can prove to be super useful not only for self-use but also for penetration testers or hackers. One might find passwords, sensitive information, or data that can be leveraged against another person. However, if you know what is online about you, that information is harder to weaponize against you.
Another note is that you are not limited to Google when searching for content online. Different search engines end up with different data, so it would be worth using dorks or similar search queries across platforms like Bing, DuckDuckGo, Yahoo, etc. You never know what one platform might have that another does not.
DeHashed/HaveIBeenPwned/ IntelX
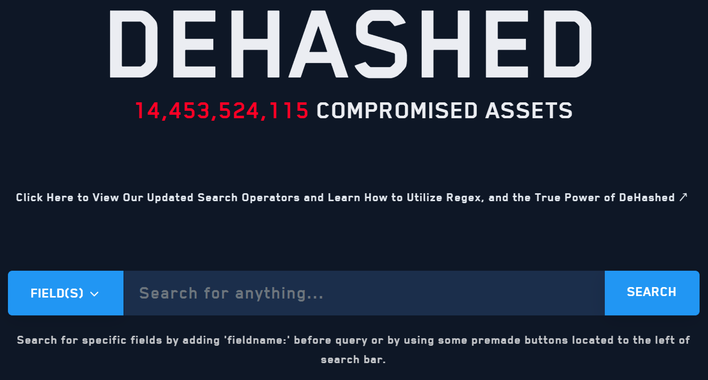
Besides simple searching for yourself, there are websites dedicated to archiving leaked data so you can search it all. The first of these is a website called DeHashed, which claims to have over 1000 data sources from breaches and leaks across the Internet. You can search this data by email, username, IP, name, address, phone number, VIN, or domain name. However, searching this data is not necessarily free, though you can get a search or two in with a free account. Besides that, accessing all this data costs just $5.49 for seven days with unlimited searches, which is fairly reasonable.
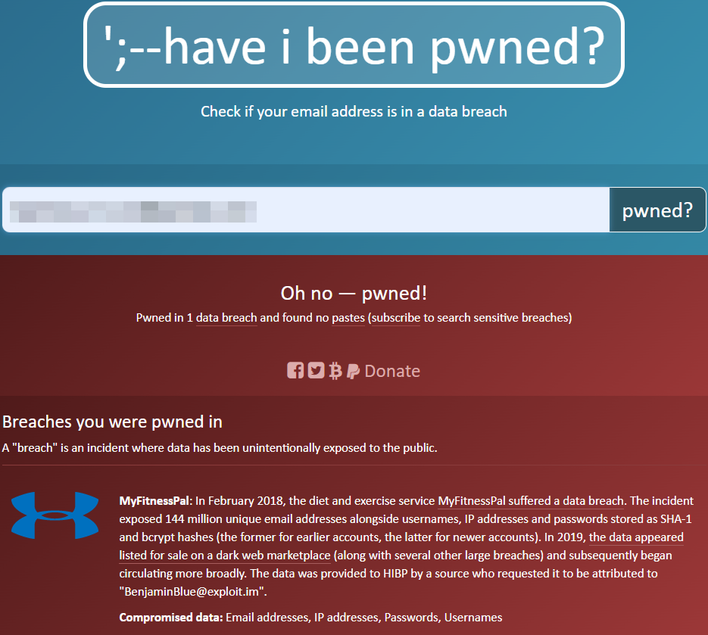
If you don’t particularly care about breach details as much, there are options such as HaveIBeenPwned. This site lets you plug in your email address or password to see if it comes up in similar data sets. If your account appears in one of the datasets, it will flag it and let you know you have been pwned (pronounced p-owned).
Finally, there is another site similar to DeHashed called IntelX which also has similar data to HaveIBeenPwned. Entering my email yielded the same results as HaveIBeenPwned but with more specificity, which could be useful in some cases. Here, it was not, but your mileage may vary.
Shodan For Discovering What Your Personal Devices Expose On The Net
In a bit of a change of pace, knowing your online presence also includes knowing what you may be exposing online in terms of IoT devices or otherwise. Before we get into that, though, you are going to need your public IP address at home, which can be found by simply Googling that and grabbing the result. Then, you can take the (likely) four-octet IPv4 address you found and plug it into Shodan.
With all this said, it should be noted that what you see on Shodan is not all your own stuff, so you need to be careful here. It is somewhat of a legally gray area, and we are not lawyers. The long and short of it is, do not go accessing computers or network devices that you do not have permission to. There may be open webcams, websites, servers, or random services that you see if you just look for them like you would search for in a regular search engine, but you do not have permission, so do not go snooping unless you know it is your own equipment you are snooping on. Better yet, perhaps this would be a good time to find a techy/cybersecurity-oriented friend who could run a network scan of your home externally and internally, yielding similar results.
People Search Engines
Further, you could also use IDCrawl or That’sThem to get some leads on your accounts. These sites are not necessarily a silver bullet to finding your information, but with them, you can start finding specific data points and corroborating them together to build the digital puzzle that is you.
OSINT Framework and Other Resources
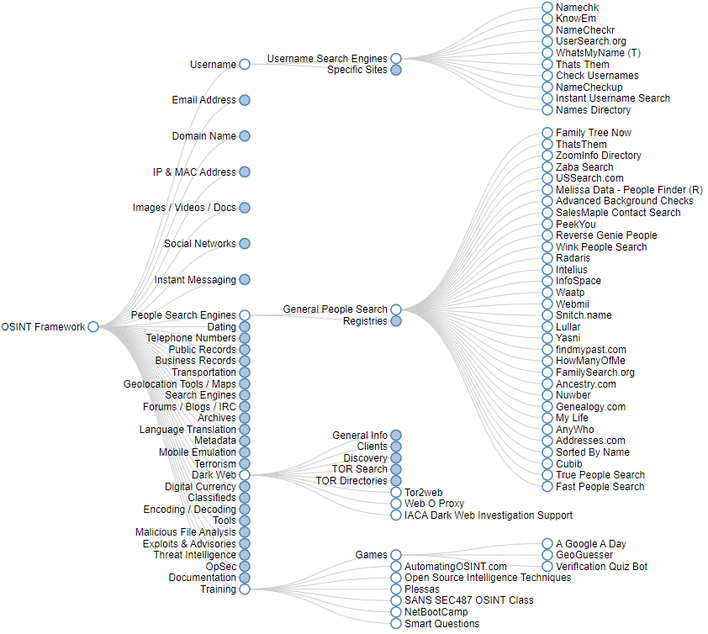
At the end of the day, there is likely to be a significant amount of data about you online, so just searching on Google for your name will not cut it. As such, using some more advanced OSINT techniques will help you figure out your digital footprint, enabling you to be a more secure and aware digital denizen.

