How GitHub Is Making It Easier To Root Out Security Flaws In Your Open Source Code
Those who follow cybersecurity news will know that both security researchers and threat actors alike are frequently discovering security vulnerabilities, prompting developers to create and release patches for these vulnerabilities. While fixing security flaws is a good thing, it’s bad news when such fixes are prompted by threat actors actively exploiting previously unknown vulnerabilities. Security researchers try to uncover vulnerabilities and report them to developers before this can happen, but researchers don’t always beat threat actors to the punch. In the hopes of aiding developers in the race to discover security vulnerabilities, the code hosting service GitHub has released an easy way for developers to scan the contents of their repositories for vulnerabilities.
This new security scanning option makes use of CodeQL, which is GitHub’s own semantic code analysis engine that powers the platform’s paid Advanced Security feature set. Up to this point, developers wanting to scan their code for vulnerabilities with the CodeQL analysis engine have had to create custom .yaml files that direct the engine to scan each repository at specified intervals. The new “default configuration” option for public repositories gives developers the choice to enable CodeQL scanning without any manual setup or subscription required.
This new security scanning option makes use of CodeQL, which is GitHub’s own semantic code analysis engine that powers the platform’s paid Advanced Security feature set. Up to this point, developers wanting to scan their code for vulnerabilities with the CodeQL analysis engine have had to create custom .yaml files that direct the engine to scan each repository at specified intervals. The new “default configuration” option for public repositories gives developers the choice to enable CodeQL scanning without any manual setup or subscription required.
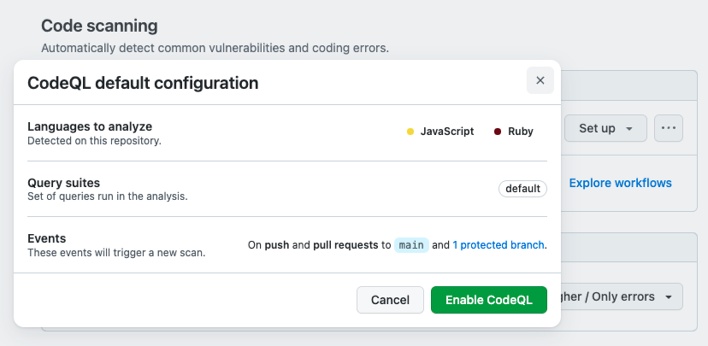
Repository maintainers can find this new option in the “Settings” tab of each repo. Under the “Security” heading is a “Code security and analysis” page that displays “Code scanning” options. Next to the “CodeQL analysis” option is a “Set up” button that prompts users to select “Default” or “Advanced.” The latter configuration options lets developers set up CodeQL scanning manually with a custom .yaml file, but developers can skip the manual setup process by choosing “Default” instead. Once selected, the default configuration prompt will display the programming languages CodeQL detects in the repository, as well as the query suites that will be run in the analysis and the events that will trigger a new scan. If these settings seem agreeable, the final step is to click “Enable CodeQL.”
According to GitHub, users will be able to customize the query suites and events in the future, but the default configuration will use a set of default options for the time being. The default configuration also currently requires that repositories contain only JavaScript/TypeScript, Python, and Ruby. The CodeQL analysis engine supports a larger list of languages, but GitHub is still working to enable them for the default configuration option. For now, developers wanting to run scans on repositories containing other languages will have to stick with the advanced configuration option.
Regardless of how CodeQL scanning is configured, it will work in the background once enabled to detect security vulnerabilities and notify developers of these flaws. Developers can then address detected vulnerabilities accordingly and hopefully before threat actors manage to exploit them.
According to GitHub, users will be able to customize the query suites and events in the future, but the default configuration will use a set of default options for the time being. The default configuration also currently requires that repositories contain only JavaScript/TypeScript, Python, and Ruby. The CodeQL analysis engine supports a larger list of languages, but GitHub is still working to enable them for the default configuration option. For now, developers wanting to run scans on repositories containing other languages will have to stick with the advanced configuration option.
Regardless of how CodeQL scanning is configured, it will work in the background once enabled to detect security vulnerabilities and notify developers of these flaws. Developers can then address detected vulnerabilities accordingly and hopefully before threat actors manage to exploit them.

