Google Chrome 88 Patches This Active Zero-Day Security Exploit, Update Immediately
Google has begun pushing out an update to its Chrome browser to patch a zero-day vulnerability that is potentially being exploited by hackers in North Korea. If you use Chrome—and many people do, as it wields the largest market share of all browsers—you should apply the update at your earliest convenience (and right now, if possible).
The update shifts Chrome to version 88.0.4324.150 and is available for builds on Windows, Mac, and Linux. At the moment, Google is restricting access to finer grain details about the zero-day vulnerability "until a majority of users are updated with a fix." However, it has been assigned CVE-2021-21148 with a High security rating.
According to what few details are available, this security flaw can result in a "heap buffer overflow in V8," which is Google's open-source JavaScript and WebAssembly engine. While Google did not get into specifics, it did acknowledge there are reports of attackers exploiting this zero-day vulnerability in the wild.
The timing of this update follows a recent report from Google's Threat Analysis Group, in which the division said it discovered an active and ongoing campaign targeting security researchers within various companies and organizations, presumably around the world. It's part of a sneaky social engineering hack.
"The actors behind this campaign, which we attribute to a government-backed entity based in North Korea, have employed a number of means to target researchers... The actors have been observed targeting specific security researchers by a novel social engineering method. After establishing initial communications, the actors would ask the targeted researcher if they wanted to collaborate on vulnerability research together, and then provide the researcher with a Visual Studio Project," the report states.
Inside the Visual Studio Project would be actual source code for exploiting the vulnerability, along with an add DLL containing custom malware. This malware would get straight to work phoning C2 domains controlled by the bad actors.
According to the report, the hackers have also been successful in spreading the custom malware by getting security researchers to visit a compromised blog post.
"In each of these cases, the researchers have followed a link on Twitter to a write-up hosted on blog.br0vvnn[.]io, and shortly thereafter, a malicious service was installed on the researcher’s system and an in-memory backdoor would begin beaconing to an actor-owned command and control server," the report adds.
Update Google's Chrome Browser Now
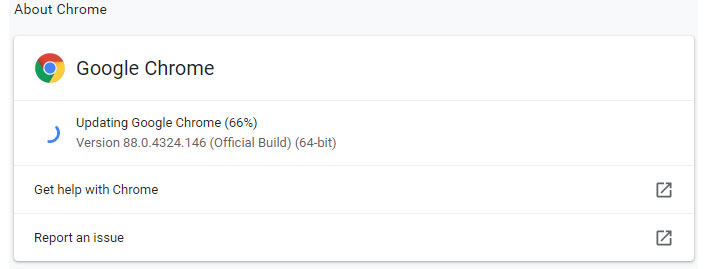
Your best bet is to update Chrome as soon as possible. This is easy enough to do—just click on the three vertically aligned dots in the upper-right corner of Chrome, then navigate to Help > About Google Chrome. The browser will then fetch the update, if it has not already been applied.
According to Stat Counter's latest data, Chrome owns a dominating 63.63 percent share of the overall browser market. The next closest is Apple's Safari browser, which sits in a distant second place with a 19.37 percent share. Firefox and Edge, meanwhile, both have a less than 4 percent share of the browser market.

