Here's How Hackers Are Using Bogus Coronavirus Maps To Infect Your Computer
Malicious actors who make it their business to spread malware obviously have no scruples about preying on on people in any manner possible, but sometimes they fall to new lows. We saw when it when hackers attempted to assault epilepsy patients by posting flashing animations to the Epilepsy Foundation's support forum in hopes of causing seizures, and now they are leveraging the coronavirus pandemic to spread malware, via a live map.
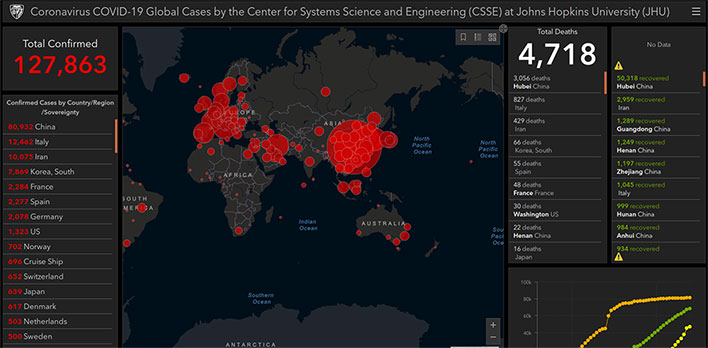
Security researcher Brian Krebs of KrebsOnSecurity found that in one such scheme, hackers are using an interactive dashboard of coronavirus infections and deaths produced by Johns Hopkins University on malicious websites, and possibly spam emails as well, to spread malware capable of stealing people's passwords.
In addition, he found that a member of several Russian-language cybercrime forums has been selling a digital corornavirus infection kit that also uses the same interactive map. It costs $200 and if the buyer already has a Java code signing certificate, or $700 if the buyer wishes to use the seller's own Java code signing certificate.
"It loads [a] fully working online map of coronavirus infected areas and other data," the seller states. "Map is resizable, interactive, and has real time data from World Health Organization and other sources. Users will think that PreLoader is actually a map, so they will open it and will spread it to their friends and it goes viral!"
Over 5,000 people have died from the coronavirus, and more than 134,000 people worldwide have been infected since it was first detected in December. Major trade shows have been shut down as a precaution, such as Mobile World Congress, and most sporting events have either been cancelled or suspended for the remaining games, including the NBA, NHL, and NCAA.
According to Check Point Security, coronavirus-themed domains are 50 percent more likely to be malicious than other domains.
"Since January 2020, based on Check Point Threat Intelligence, there have been over 4,000 coronavirus-related domains registered globally. Out of these websites, 3% were found to be malicious and an additional 5% are suspicious. Coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period, and also higher than recent seasonal themes such as Valentine’s day," Check Point stated in a blog post.
It's just a bad situation all around. What can you do? Well, be cautious of which sites you are visiting, and be extra diligent about practicing common sense computing habits (don't download unexpected email attachments, type URLs directly into your browser rather than clicking on hyperlinks, and so forth). And if you want to be proactive, you can donate CPU/GPU cycles to Folding@home, a distributed computing project that has begun focusing on the coronavirus.

