According to a threat analysis by Palo Alto Networks' Unit 42, a deceptive phishing technique called domain shadowing is on the rise. It may even be more prevalent than previously assumed by information security experts. Between April 25 and June 27 of 2022, the company found that 12,197 domains were shadowed to provide malicious content.
A shadow domain is usually a subdomain surreptitiously added on to a typically reputable domain that will portray something that might look legitimate when it is not. So, for example, if you were to go to something like "yourbank[.]com" and asked to log in to your account, you might think nothing of it. However, shadowed domains might present as thisisactuallybad[.]yourbank[.]com. This page might be used to steal your login information with a similar end result to the fake
steam login browsers we recently reported on.
The report goes on to point out that detecting shadowed domains is quite difficult to do. In many cases, subdomains are often easily and quickly configured, and usually intentionally. For example, web design firms will intentionally ask for a subdomain if their client needs a redesign to use for testing. In other cases, it may be a legitimately added service that becomes hijacked. The method used for automatic detection from Unit 42 involves several conditions needing to be met. It checks conditions such as verifying if the subdomains match the patterns of other subdomains on the domain, if the IP address that the subdomain points to is significantly different from the original, how long the subdomain has been active, and more.
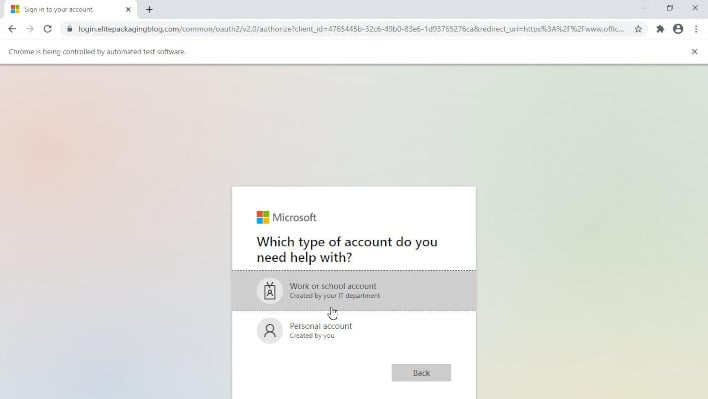
 Screenshot of a false login shown from a shadowed domain
Screenshot of a false login shown from a shadowed domain
There are a few ways to look out for shadow domains yourself. If you're a domain owner, you can check to see if you have any subdomains you don't recognize on your DNS records. If you do, change your password and, in some cases, your security access, then remove those subdomains. If you're a general user, pay very close attention to the address you're following a link for if it's in your e-mail, and pay close attention to who actually sent the message. Also, if you are prompted with a login, double check the address bar—if you are not entirely familiar with the entire domain name, including the subdomain, do not log in. You may even with to contact the institute in which you're trying to access their web site to confirm details through your own means. For example, if it is your bank, call your bank using the number on your statements. You can read the full report from Unit 42 by
clicking here.