Hackers Can Track You And Steal Your Data With Wi-Fi Probing, How To Protect Yourself
Wi-Fi capable devices, like smart phones, often automatically send out probe requests in order to detect available Wi-Fi networks in the area. These probe requests include a device identifier known as a MAC address. Nowadays, most phones, as well as some other devices, utilize randomized MAC addresses to increase privacy, as a non-randomized persistent MAC address uniquely identifies a device for as long as it is in operation, making it easy to track over time. Some cities and stores conduct location tracking by picking up Wi-Fi probe requests from phones and triangulating their locations.
Wi-Fi probe requests are sent out in bursts, and phones that employ MAC address randomization send out each burst with a different MAC address. Wi-Fi location tracking can’t rely on MAC addresses to identify and track devices over time when the MAC addresses are constantly changing. However, Wi-Fi probe requests can contain additional information that could be used for tracking.
Wi-Fi probe requests are sent out in bursts, and phones that employ MAC address randomization send out each burst with a different MAC address. Wi-Fi location tracking can’t rely on MAC addresses to identify and track devices over time when the MAC addresses are constantly changing. However, Wi-Fi probe requests can contain additional information that could be used for tracking.
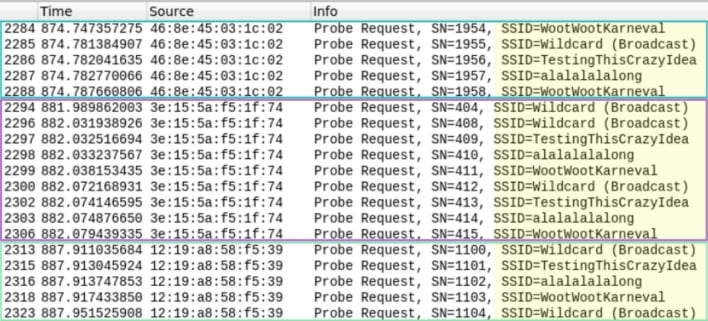
Researchers at the University of Hamburg have published a paper drawing attention to the fact that probe requests can include a device’s preferred network list (PNL), which is a list of previously connected Wi-Fi networks. Wi-Fi networks are identified in a PNL by their Service Set Identifiers (SSIDs), which are the Wi-Fi network names that appear in a device’s Wi-Fi settings. Unlike randomized MAC addresses, PNLs stay consistent over time, which means that they could be used to identify and track devices. The image above shows three Wi-Fi probe request bursts sent by the same device, and, while the MAC address is different for each burst, the list of previously connected Wi-Fi networks remains the same. Someone detecting nearby probe requests could pick out these three bursts as coming from the same device, despite the randomized MAC addresses.
The researchers demonstrated how this kind of device tracking could be accomplished by setting up networking equipment in a busy pedestrian area in a German city and logging probe requests for one hour at a time. The researchers conducted this experiment three times, then analyzed the data. By comparing the SSIDs broadcast with some of the probe requests, the researchers were able to uniquely identify 362 devices that employed randomized MAC addresses.
The researchers also highlighted a further potential privacy concern associated with broadcasting Wi-Fi network SSIDs along with probe requests. Geo-location services, like Google’s, rely on mapping the location of Wi-Fi access points, and there are publicly available datasets with GPS coordinates tied to Wi-Fi networks. Using one such database, the researchers were able to pinpoint 334 of the SSIDs logged by their equipment to unique locations. Someone snooping on nearby probe requests could use this technique to find where passersby live or work, as the Wi-Fi networks at those locations are likely to be in the PNLs of people’s phones.
The researchers demonstrated how this kind of device tracking could be accomplished by setting up networking equipment in a busy pedestrian area in a German city and logging probe requests for one hour at a time. The researchers conducted this experiment three times, then analyzed the data. By comparing the SSIDs broadcast with some of the probe requests, the researchers were able to uniquely identify 362 devices that employed randomized MAC addresses.
The researchers also highlighted a further potential privacy concern associated with broadcasting Wi-Fi network SSIDs along with probe requests. Geo-location services, like Google’s, rely on mapping the location of Wi-Fi access points, and there are publicly available datasets with GPS coordinates tied to Wi-Fi networks. Using one such database, the researchers were able to pinpoint 334 of the SSIDs logged by their equipment to unique locations. Someone snooping on nearby probe requests could use this technique to find where passersby live or work, as the Wi-Fi networks at those locations are likely to be in the PNLs of people’s phones.
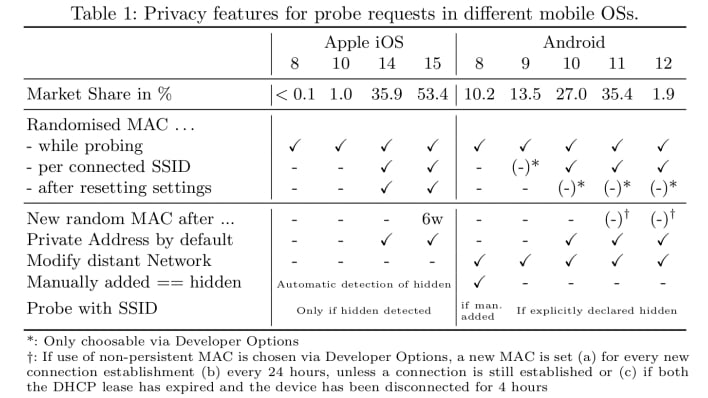
Fortunately, PNLs are no longer included in probe requests of most phones, unless the networks are marked as hidden networks. However, Android version 8 considers any Wi-Fi network manually added by the user as a hidden network and will broadcast the SSIDs with probe requests, and devices running Android 8 still account for 10.2% of the global smartphone market share.
An unfortunate result of Android 8 including specifically manually added SSIDs with probe requests is that it broadcasts information mistakenly entered into the SSID field. Among the 58,489 SSIDs logged by the researchers were character strings likely to be default Wi-Fi passwords for FritzBox and Telekom routers, as well as 106 names and three email addresses.
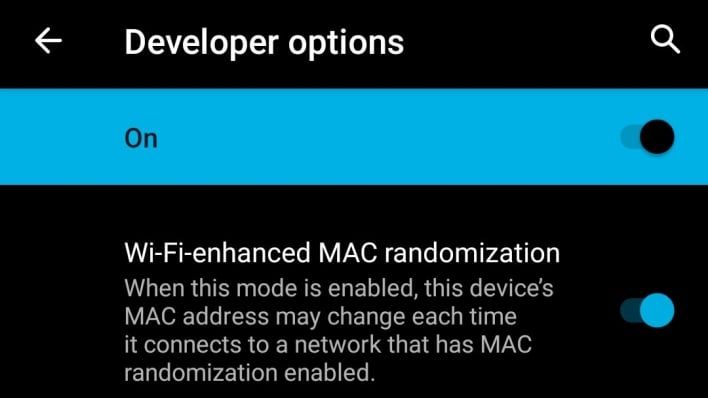
Users wanting to preserve their privacy shouldn’t use phones still running Android 8. iOS 15 and Android 11 and newer contain the strongest probe request privacy protections, making them the preferred options for avoiding probe request device identification and location tracking. Users can also prevent their devices from sending out Wi-Fi probe requests while out in public by disabling Wi-Fi. Lastly, users running Android 11 and up can go into developer options and enable the enhanced MAC randomization feature to further increase their privacy protections.
You can read more about the researchers’ findings in their paper (PDF).
You can read more about the researchers’ findings in their paper (PDF).

