How Hackers Are Poisoning PNG Images With Malware Payloads

ESET are the ones who located this technique, which was used to attack energy companies in Central and Southeast Asia. To be clear, it was used on machines that were already compromised, so a different exploit was used to gain access to the systems and initially infect them.

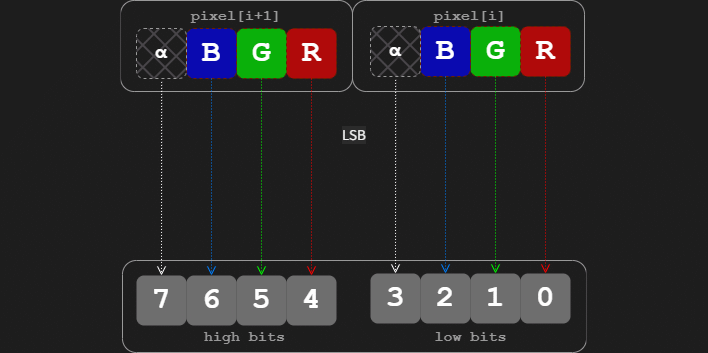
By using the least-significant bits that have the smallest impact on the image's appearance, you can set them to whatever value you want without changing the image's apparent legitimacy. In turn, this ability allows you to encode whatever binary data you want into a PNG image that for all intents and purposes is still a completely legitimate image, even under simple analysis.
In the specific event that ESET and Avast chronicled, executable data encoded in PNG images allowed the attackers to then install the DropBoxControl malware and transfer files in encrypted format between the infected systems and DropBox.
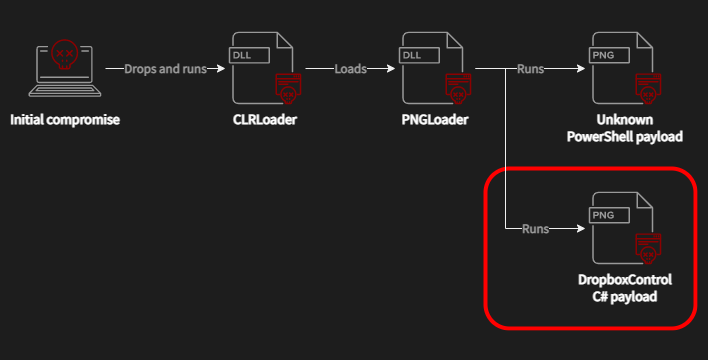
As we mentioned, these images appear to be completely legitimate for all purposes; while "least significant bit" encoding is well-known and easily found via statistical analysis, you need to be looking for it to find it. Fortunately you can't attack a system just with these images, so there's no particular cause for alarm—yet.