Hertzbleed Boost Clock Snooping Security Flaw Steals Crypto Keys From AMD And Intel CPUs

If you own a modern desktop PC or laptop, or even one that's a bit older, you're probably affected by a newly discovered family of side-channel attack vectors that have been dubbed Hertzbleed. In separate security advisories, Intel confirmed that all of its x86 processors including Alder Lake are vulnerable to Hertzbleed, and AMD stated that most of its chips are too, including its latest-generation Ryzen processors based on Zen 3. The verdict is still out on whether Arm-based processors are affected.
Researchers from the University of Texas at Austin, University of Illinois Urbana-Champaign, and University of Washington outlined their startling findings in a paper and tackled some of the more pressing questions in a separate FAQ. Simply put, in a worst case scenario an attacker could leverage a flaw in most x86 processors to extract cryptographic keys from remote servers that were previously thought to be secure.
"Under certain circumstances, the dynamic frequency scaling of modern x86 processors depends on the data being processed. This means that, on modern processors, the same program can run at a different CPU frequency (and therefore take a different wall time) when computing, for example, 2022 + 23823 compared to 2022 + 24436," the researchers explain.
The researchers say this not a bug in a true sense of the term, but a feature of modern processors. That feature is dynamic frequency scaling, which you might recognize as throttling to stay within pre-configured power and thermal limits.
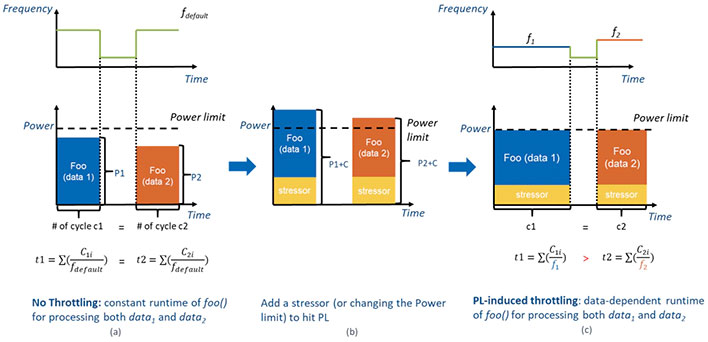
Power management reactive limits throttling converts power differences to frequency/timing differences (Source: Intel)
Dynamic voltage and frequency scaling (DVFS) is not dependent on a specific microarchitecture and is a key part of all modern x86 processors from AMD and Intel. While the researcher paper dives into the weeds of how Hertzbleed works, the high level overview is that an attacker could figure out the changes in a target CPU's power consumption by calculating the power profile of certain workloads, namely cryptographic ones, and use that timing data to steal cryptography keys.
It's a bit more involved than that, but the bottom line according to the researchers is that "Hertzbleed is a real, and practical, threat to the security of cryptographic software." And to an extent, AMD and Intel agree, though both have attached a "Medium" security rating to the attack vector and neither one is planning to release a patch.
"As the vulnerability impacts a cryptographic algorithm having power analysis-based side channel leakages, developers can apply countermeasures on the software code of the algorithm. Either masking1,2,3, hiding3 or key-rotation may be used to mitigate the attack," AMD states in a security advisory.
Intel has also provided software guidance for cryptographic developers to "harden their libraries and applications" against these types of attacks, such as adding "dummy instructions that introduce sufficient power or latency variation." Adding random noise in this manner would make it more difficult for a hacker to leverage this type of side-channel attack.
Alternatively, those who are worried about this could disable Turbo Boost on Intel chips and Turbo Core or Precision Boost on AMD processors to effectively mitigate Hertzbleed. However, doing so has a significant impact on performance.

