Alarming IceBreaker Malware Gives Hackers A Backdoor Into Gaming And Gambling Websites

We often report on phishing campaigns involving fraudulent customer support agents who trick victims into giving up sensitive information or installing malware on their systems. However, sometimes threat actors flip this script, instead posing as customers in need of help in order to prey on customer support agents. The cybersecurity firm Security Joes has published research detailing the attack chain of a new threat actor the researchers have dubbed “IceBreaker APT.” This threat actor has been targeting online gaming/gambling websites with its own IceBreaker Backdoor malware.
The attack chain for this malware begins with a social engineering attempt in which the threat actors contact a website’s customer support and claim to be experiencing an issue with the website that needs troubleshooting. The threat actors vaguely describe the supposed problem, saying that it would be easier to share a screenshot showing an unexpected error or prompt. In some cases, the threat actors claim to be non-English speakers, which may serve to assure customer support agents that viewing a screenshot would be a better way to understand the problem.
The attack chain for this malware begins with a social engineering attempt in which the threat actors contact a website’s customer support and claim to be experiencing an issue with the website that needs troubleshooting. The threat actors vaguely describe the supposed problem, saying that it would be easier to share a screenshot showing an unexpected error or prompt. In some cases, the threat actors claim to be non-English speakers, which may serve to assure customer support agents that viewing a screenshot would be a better way to understand the problem.
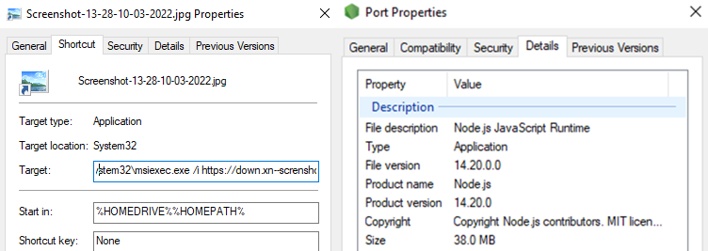
The threat actors then link to a ZIP file stored in DropBox or at a domain name imitating that of a legitimate file sharing website using not-Latin characters. Customer service agents who download and unzip this file will find a LNK shortcut file disguised as a JPEG screenshot. When opened, this LNK file quietly connects to a command-and-control (C2) server controlled by the threat actors, downloads a MSI installer file, and runs the installer. This MSI package contains a collection of decoy files, which it uses to pose as a legitimate software installer and obscure the real payload, which is an archived executable file named “Port.exe.”.
The MSI installer extracts and executes this file, infecting the system with the IceBreaker Backdoor. This malware is written in JavaScript and is fairly unique in using the Node.js runtime environment. The researchers are still analyzing this piece of malware but have so far determined that it possesses the following capabilities:
The MSI installer extracts and executes this file, infecting the system with the IceBreaker Backdoor. This malware is written in JavaScript and is fairly unique in using the Node.js runtime environment. The researchers are still analyzing this piece of malware but have so far determined that it possesses the following capabilities:
- Customization via plugins that extend the build-in features of the threat.
- Process discovery.
- Steal passwords and cookies from the local storage. It particularly targets Google Chrome.
- Enables a Socks5 reverse proxy server in the infected machine via the open source project tsocks.
- Persistence is achieved by creating a new LNK file in the startup folder "\Microsoft\Windows\Start Menu\Programs\Startup\WINN.lnk".
- Exfiltrate files to the remote server via web sockets.
- Run custom VBS scripts in the infected machine.
- Take screenshots from the victim's machine.
- Generate remote shell sessions.

