Apple iOS 11.2 HomeKit Exploit Left Smart Home Locks And Garage Door Openers Vulnerable
The vulnerability was first brought to public light by 9to5Mac, and is reportedly highly difficult to reproduce. Nonetheless, it allows for an unauthorized user to gain control of smart home devices connects via HomeKit. Given that the connected-accessories that are compatible with HomeKit extend to security cameras, smart locks, garage door openers and thermostats, the potential for abuse cannot be taken lightly.
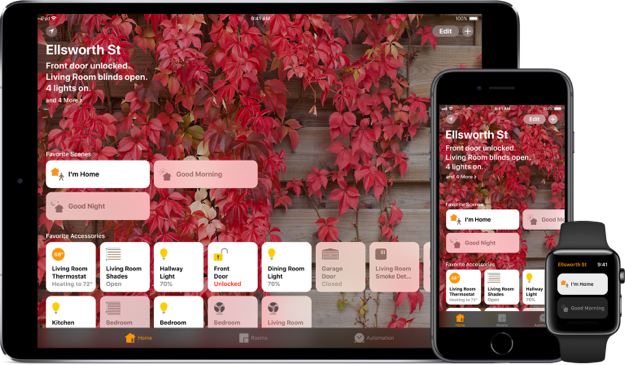
9to5Mac has been careful not to describe in great detail the mechanics behind the vulnerability, but it does explain:
The issue was not with smart home products individually but instead with the HomeKit framework itself that connects products from various companies...The issue was not with smart home products individually but instead with the HomeKit framework itself that connects products from various companies.
For now, Apple has applied a server-side fix that closes the vulnerability, but it has the side effect of breaking some HomeKit functionality. Apple has confirmed, however, that an iOS 11.2 update arriving next week will restore any broken functionality.
Apple came under fire in late November after a password exploit that allows anyone to bypass administrator authentication to login to a Mac running macOS 10.13 High Sierra. Apple quickly issued a fix for the exploit, but it embarrassingly broke file sharing for many users as a result. To make matters worse, users on earlier versions of macOS High Sierra that had applied the security patch, and then later upgraded to High Sierra 10.13.1 saw the effects of the patch erased.

