Iranian Hacker Group Pivots Targets To Support Hostile IRGC Operations

The cuteness of kittens is widely recognized and appreciated on the internet, but there’s nothing cute about the Iranian Advanced Persistent Threat (APT) known as “Charming Kitten.” Also known as TA453 or APT42, this threat group has been conducting cyber espionage at the behest of the Iranian regime since at least 2017, if not earlier. New research by Proofpoint documents more recent activity attributable to TA453 that deviates from the group’s standard activity in terms of both tactics and targets. Proofpoint contends that this uncharacteristic activity aligns specifically with the operations of the Islamic Revolutionary Guard Corps (IRGC), which is just one faction within the complex balance of power that constitutes the current Iranian regime.
From what cybersecurity researchers can tell, TA453 is composed of multiple subgroups. Using various markers, Proofpoint currently tracks roughly six subgroups. However, regardless of subgroup, TA453 has historically targeted academics, researchers, diplomats, dissidents, journalists, and human rights workers with phishing attacks. These phishing attacks typically take the form of protracted conversations between the threat actor and the target concerning benign topics. Sometimes these discussions will continue for weeks before the threat actor finally sends a link to a malicious webpage asking the target to enter login credentials. Any credentials entered here end up in the hands of TA453, which the group leverages to access targets’ email accounts and exfiltrate email content.
However, since late 2020, Proofpoint has observed TA453 using tactics and targeting individuals that fall outside of the group’s regular purview. The threat group usually uses email accounts created specifically for use in phishing attacks, but some of TA453’s more recent attacks have made use of compromised email accounts. Proofpoint has also observed the APT using multiple sock-puppet accounts to engage in what appear to its targets to be conversations involving multiple different people.
From what cybersecurity researchers can tell, TA453 is composed of multiple subgroups. Using various markers, Proofpoint currently tracks roughly six subgroups. However, regardless of subgroup, TA453 has historically targeted academics, researchers, diplomats, dissidents, journalists, and human rights workers with phishing attacks. These phishing attacks typically take the form of protracted conversations between the threat actor and the target concerning benign topics. Sometimes these discussions will continue for weeks before the threat actor finally sends a link to a malicious webpage asking the target to enter login credentials. Any credentials entered here end up in the hands of TA453, which the group leverages to access targets’ email accounts and exfiltrate email content.
However, since late 2020, Proofpoint has observed TA453 using tactics and targeting individuals that fall outside of the group’s regular purview. The threat group usually uses email accounts created specifically for use in phishing attacks, but some of TA453’s more recent attacks have made use of compromised email accounts. Proofpoint has also observed the APT using multiple sock-puppet accounts to engage in what appear to its targets to be conversations involving multiple different people.
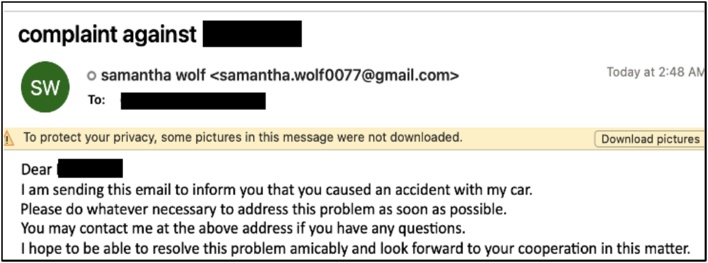
Some of TA453’s phishing attacks have also involved confrontational social engineering lures, which is atypical for the threat group. Rather than the group’s usual benign discussions, some targets have received vaguely threatening messages or a out-of-the-blue emails accusing them of wrecking someone’s car. TA453 sends many of these sorts of emails from accounts associated with one particular persona known as “Samantha Wolf.”
Since 2021, or possibly 2020, some of TA453’s phishing emails have included the addition of attachments with malicious payloads. Cybersecurity researchers have found the threat group using a PowerShell backdoor known as GhostEcho, as well as an email exfiltration tool called HYPERSCRAPE. GhostEcho is particularly notable, as it appeared to be under active development for some time, demonstrating that TA453 is not only willing to use malware, but also capable of developing it.
TA453 deployed these atypical tactics against a variety of uncharacteristic targets, including medical researchers, an aerospace engineer, a Realtor, and travel agencies. According to Proofpoint, these targets seem to align with operations conducted by the IRGC and may indicate that a subgroup of TA453 is operating under a directive to support specific IRGC operations.
For example, TA453’s targeting of an aerospace engineer aligns with the IRGC’s efforts to embed itself in Iran’s space program. The targeting of a seemingly random Florida Realtor also makes sense in light of the fact that the Realtor in question was involved in the sale of homes near the headquarters of US Central Command (CENTCOM). CENTCOM is responsible for military operations in the Middle East, and the IRGC works to prevent foreign interference. In a statement to HotHardware, the VP of threat research and detection at Proofpoint, Sherrod DeGrippo, stated that “All this serves as a window into aims of the Islamic Revolutionary Guard Corps (IRGC) and the flexible mandate under which TA453 works.”
Since 2021, or possibly 2020, some of TA453’s phishing emails have included the addition of attachments with malicious payloads. Cybersecurity researchers have found the threat group using a PowerShell backdoor known as GhostEcho, as well as an email exfiltration tool called HYPERSCRAPE. GhostEcho is particularly notable, as it appeared to be under active development for some time, demonstrating that TA453 is not only willing to use malware, but also capable of developing it.
TA453 deployed these atypical tactics against a variety of uncharacteristic targets, including medical researchers, an aerospace engineer, a Realtor, and travel agencies. According to Proofpoint, these targets seem to align with operations conducted by the IRGC and may indicate that a subgroup of TA453 is operating under a directive to support specific IRGC operations.
For example, TA453’s targeting of an aerospace engineer aligns with the IRGC’s efforts to embed itself in Iran’s space program. The targeting of a seemingly random Florida Realtor also makes sense in light of the fact that the Realtor in question was involved in the sale of homes near the headquarters of US Central Command (CENTCOM). CENTCOM is responsible for military operations in the Middle East, and the IRGC works to prevent foreign interference. In a statement to HotHardware, the VP of threat research and detection at Proofpoint, Sherrod DeGrippo, stated that “All this serves as a window into aims of the Islamic Revolutionary Guard Corps (IRGC) and the flexible mandate under which TA453 works.”

