Israeli Soldiers Tricked Into Installing Android Malware Via Hamas Honey Trap Scheme
Imagine hitting it off with a love (or lust) interest, and then finding out the person who grabbed your attention never existed, at least not in the way you thought. Such a situation recently happened to hundreds of Israeli soldiers who fell prey to a "honey trap" campaign and contracted digital infections on their mobile phones.
Hamas cyber militants made a bunch of fake profiles on various social media sites and chat services, including Facebook, Instagram, WhatsApp, and Telegram, and used pictures of teenage girls for the profile photos to lure soldiers into the scam. Through instant messaging exchanges, soldiers were duped into downloading dating apps containing malware.
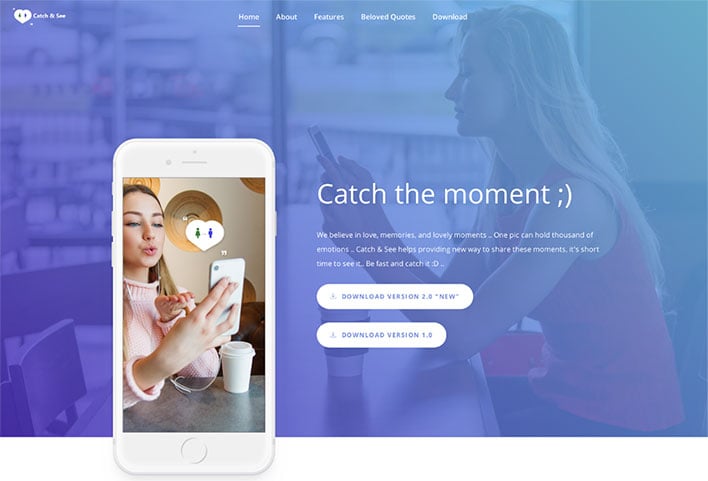
Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
— Israel Defense Forces (@IDF) February 16, 2020
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.#CatfishCaught
"Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system," Israel Defense Forces (IDF) stated on Twitter.
The malware disguised itself as three different dating apps, including GrixyApp, ZatuApp, and Catch&See. All three had accompanying websites to make them look legit. When a soldier would click on a link to download the supposed app, a message would appear saying, "the device is not supported, app will be uninstalled."
At that point, the damage was done. Security firm Check Point says the malware was capable of collecting certain device information, including IMSI and phone numbers, installed applications, and storage information, and then sent the data to a command and control server.
What was potentially more harmful, though, was the malware's ability to register as an admin on the device. This would give the culprits access to key information and features, such as the camera, calendar, location, SMS exchanges, contact lists, and browser history.
"The main functionality of this malware is to collect data on the victim such as phone number, location, SMS messages and more, while having the capability to extend its code via a received command. The command can provide the application with a URL to a DEX file, which is then downloaded and executed," Check Point explains.
This was a pretty big campaign. For every soldier who was targeted, there was an actual human at the other end trying to pull off the scheme. In some cases, soldiers were unwittingly in contact with a Hamas operator for an entire year.
"This campaign serves as a sharp reminder that effort from system developers alone is not enough to build a secure Android eco-system," Check Point says.