Massive Kaseya Ransomware Incident Has Awakened An Army Of Malware Scammers

Customers of Kaseya's Vector Signal Analysis (VSA) software are being warned to be on the lookout for phishing emails claiming to offer up a security update, but in reality contain a malicious payload. The phishing campaign is a result of a massive supply chain ransomware attack that spread through software created by the Florida-based IT company.
Notorious hacking group REvil was behind the attack, which exploited vulnerabilities in Kaseya's VSA software to distribute ransomware. In the aftermath, Kaseya said the attack affected fewer than 60 customers, though also noted that many of those customers provide IT services to multiple other companies.
"We understand that the total impact thus far has been to fewer than 1,500 downstream businesses. We have not found any evidence that any of our SaaS [software-as-a-service] customers were compromised," Kaseya said in a statement.
Kaseya is currently in the process of reviewing the full scope of the attack, and how it can prevent similar incidents from happening in the future. That includes "adding a lot more rigor to our processes, to our deployment, to the codebase to keep everyone safe, and to improve the overall security posture of our products."
While the investigation takes place, however, opportunistic malware actors are trying to lure victims into installing malicious code, under the guise of a security update.
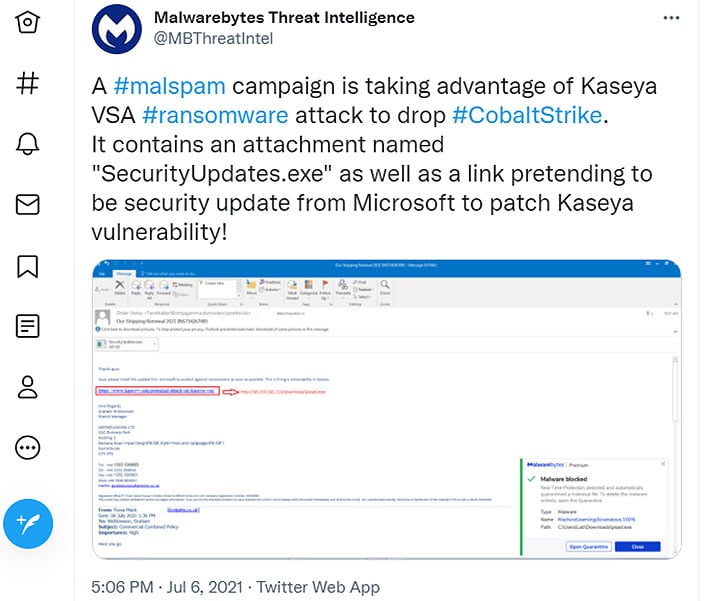
"A #malspam campaign is taking advantage of Kaseya VSA #ransomware attack to drop #CobaltStrike.
It contains an attachment named 'SecurityUpdates.exe' as well as a link pretending to be security update from Microsoft to patch Kaseya vulnerability!," Malwarebytes stated on Twitter.
Kaseya is also warning of this behavior, telling customers it is aware of bad actors sending out fake email notifications designed to appear as official Kaseya updates, when in fact they are not.
"These are phishing emails that may contain malicious links and/or attachments," Kaseya says. "Do not click on any links or download any attachments in emails claiming to be a Kaseya advisory. Moving forward, all new Kaseya email updates will not contain any links or attachments."
Kaseya highlight keys parts of its communication in bold to drive the point home. And according to Malwarebytes, at least one of the phishing campaigns attempts to trick victims into installing a Windows executable file containing a Cobalt Strike payload. Cobalt Strike is a penetration testing tool that is one of the most popular ones being abused by cybercriminals.
On the bright side, Kaseya says it patched the security holes that REvil took advantage of and has implemented additional security measures as well.