LAPSUS$ Hackers Stole T-Mobile Source Code But The FBI Schooled Them And Stole It Back
Some recent revelations regarding cybercriminal activity have spelled bad news for T-Mobile. After government authorities seized RaidForums, a popular hacking site where stolen data was sold, court records revealed that T-Mobile attempted to buy back stolen customer data. However, the deal went sideways when the thieves broke the conditions of the agreement by continuing to sell the data. Now leaked chat messages show that LAPSUS$ stole T-Mobile source code.
LAPSUS$ was a hacking group that recently stole source code from a number of big name targets, including NVIDIA, Samsung, and Microsoft. Shortly after this string of high profile data thefts, British police arrested seven individuals over involvement with the hacking group. The suspects all fell between the ages of 16 and 21 years old. The leader, who is known as “White,” turned out to be only 16 years old and living with his mother.
LAPSUS$ was a hacking group that recently stole source code from a number of big name targets, including NVIDIA, Samsung, and Microsoft. Shortly after this string of high profile data thefts, British police arrested seven individuals over involvement with the hacking group. The suspects all fell between the ages of 16 and 21 years old. The leader, who is known as “White,” turned out to be only 16 years old and living with his mother.
That said, while the primary members of LAPSUS$ may now be behind bars, details of their exploits are still forthcoming. Leaked chat messages obtained by Brian Krebs show that LAPSUS$ breached T-Mobile systems back in March. On multiple occasions, the hackers were able to use social engineering techniques to fool T-Mobile employees into giving LAPSUS$ computers access to the company’s virtual private network (VPN).
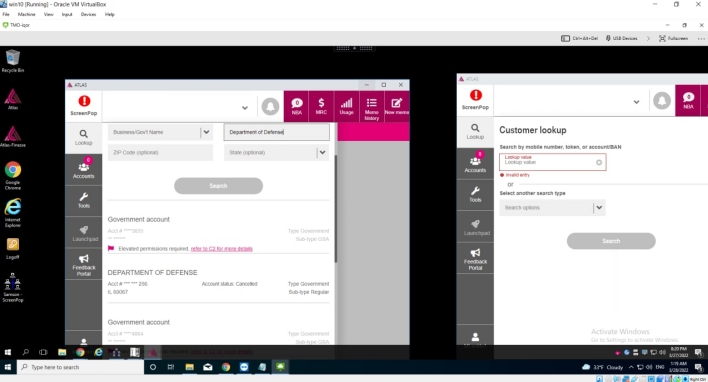
LAPSUS$ leveraged access to T-Mobile’s systems to perform SIM swap attacks, reassigning customers’ phone numbers to devices controlled by the hackers. Such attacks give bad actors access to victims’ text messages, which are still a common avenue for multi-factor authentication codes. The hackers eventually searched for T-Mobile phone numbers associated with the FBI and Department of Defense, but accessing these numbers required elevated permissions not available to LAPSUS$.
LAPSUS$ leveraged access to T-Mobile’s systems to perform SIM swap attacks, reassigning customers’ phone numbers to devices controlled by the hackers. Such attacks give bad actors access to victims’ text messages, which are still a common avenue for multi-factor authentication codes. The hackers eventually searched for T-Mobile phone numbers associated with the FBI and Department of Defense, but accessing these numbers required elevated permissions not available to LAPSUS$.
Rather than attempt to SIM swap government phone numbers, LAPSUS$ instead pivoted to stealing T-Mobile source code. In roughly 12 hours, LAPSUS$ downloaded 38,588 T-Mobile code repositories. However, afraid of police raiding their homes, the hackers never stored any stolen source code on any of their own servers. LAPSUS$ instead used virtual private server (VPS) providers to store its stolen data.
This approach came back to bite LAPSUS$ when the FBI seized the Amazon Web Services (AWS) server that the group was using to store the stolen T-Mobile code. White initially dismissed the seizure until another member informed him that they had never made a backup of the server, prompting a distraught response from the group’s leader. The hackers frantically tried to re-download the source code, but found that their access token was no longer valid. White guessed that Gitlab auto-revoked the token, noting that “Cloning 30k repos four times in 24 hours isn’t very normal.”
As far as we know, LAPSUS$ never leaked any T-Mobile source code, thanks to the FBI. Nonetheless, the fact that the amateur hackers were able to repeatedly gain access to internal T-Mobile systems is still concerning.
T-Mobile issued the following statement in response questions by Krebs: “Several weeks ago, our monitoring tools detected a bad actor using stolen credentials to access internal systems that house operational tools software. The systems accessed contained no customer or government information or other similarly sensitive information, and we have no evidence that the intruder was able to obtain anything of value. Our systems and processes worked as designed, the intrusion was rapidly shut down and closed off, and the compromised credentials used were rendered obsolete.”
This approach came back to bite LAPSUS$ when the FBI seized the Amazon Web Services (AWS) server that the group was using to store the stolen T-Mobile code. White initially dismissed the seizure until another member informed him that they had never made a backup of the server, prompting a distraught response from the group’s leader. The hackers frantically tried to re-download the source code, but found that their access token was no longer valid. White guessed that Gitlab auto-revoked the token, noting that “Cloning 30k repos four times in 24 hours isn’t very normal.”
As far as we know, LAPSUS$ never leaked any T-Mobile source code, thanks to the FBI. Nonetheless, the fact that the amateur hackers were able to repeatedly gain access to internal T-Mobile systems is still concerning.
T-Mobile issued the following statement in response questions by Krebs: “Several weeks ago, our monitoring tools detected a bad actor using stolen credentials to access internal systems that house operational tools software. The systems accessed contained no customer or government information or other similarly sensitive information, and we have no evidence that the intruder was able to obtain anything of value. Our systems and processes worked as designed, the intrusion was rapidly shut down and closed off, and the compromised credentials used were rendered obsolete.”