LinkedIn's New "Intro" Service Is A Catastrophic Security Failure Waiting To Happen
Making money while running a social media service is difficult. Companies like Facebook and Twitter have struggled to monetize their platforms on both desktop and mobile, while striking balances that don't royally tick off users with obnoxious advertising. But in a world where dubious advertising and branding experiments are often celebrated like Nobel Prizes, LinkedIn has just launched one of the worst. It's called "Intro," and it's a security nightmare waiting to happen.
Here's the backstory. Apple locks down its iOS Mail program tightly. This isn't just because Apple loves a walled garden, though it does, but because giving developers too much access to such a vital part of the platform could compromise malware security. LinkedIn has published a lengthy breakdown of how they've defeated this process and made your email service fundamentally less secure in doing so, all in the name of bringing you clickable profiles within an email address, like so:
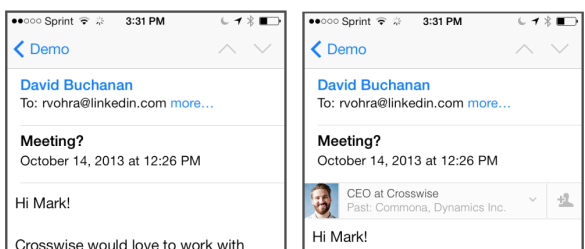
Man in the Middle:
Here's the problem. What LinkedIn does is redirect all email you receive across its own IMAP servers, as shown below.

The company is at least up-front about this, writing: "Normally your device connects directly to the servers of your email provider (Gmail, Yahoo, AOL, etc.), but we can configure the device to connect to the Intro proxy server instead."
Note that this isn't just a service for LinkedIn users communicating over LinkedIn's proprietary email service. If it was, there wouldn't be so much of a problem. The idea here is that LinkedIn can cross-reference and inject profile information about people communicating with you who also happen to have LinkedIn profiles. The company explains a little more in the same post, writing: "The Intro proxy server speaks the IMAP protocol just like an email provider, but it doesn’t store messages itself. Instead, it forwards requests from the device to your email provider, and forwards responses from the email provider back to the device. En route, it inserts Intro information at the beginning of each message body — we call this the top bar."
What LinkedIn is describing here is a classic man-in-the-middle attack in which an organization intercepts data between Points A and B by secretly positioning itself to snoop on the data stream. Granted, LinkedIn isn't doing this in secret -- but that's still the fundamental security flaw. If you use your email for anything remotely confidential, LInkedIn is now sitting in a position to retain a copy. And since their own server is now the pass-through point for your authentication credentials and security data, you're going to have a hard time keeping anything private.
A blog post at Bishop Fox goes on to detail the problems with this program, which are legion. You're changing the cryptographic signature of your own email (or allowing LinkedIn) to change it, you're connecting to a third-party to provide a vital link in a service, LinkedIn is making changes to the way your iPhone operates that could be exploited to compromise its security at a later date, the company's privacy policy is vague, it's already under investigation for spamming address books and lifting data out of other email providers without permission, and the company had 6.5 million passwords stolen last year. (LinkedIn denies the allegation).
Belatedly, the company appears to have realized it might as well have hung a sign over the door reading: "Welcome NSA, Hackers, Ne'er Do-Wells!" It has since pledged to respect its own privacy policy, made vague comments about creating a new Mail profile on the iPhone but left old profiles unaffected (as though this would impact the fact that your mail was still being fed through the proxy service) and pledges really, really, good security. Like, totally the best.
This is a terrible idea. Do not sign up for an email service with a company that already engages in shady "recruitment" tactics and scans open browser windows without your consent. Don't trust the security of a company with massive password breach issues. And don't tell corporate IT that you think this sounds like a fine and dandy idea unless you're trying to make your Sysadmin drop dead of a coronary.
Here's the backstory. Apple locks down its iOS Mail program tightly. This isn't just because Apple loves a walled garden, though it does, but because giving developers too much access to such a vital part of the platform could compromise malware security. LinkedIn has published a lengthy breakdown of how they've defeated this process and made your email service fundamentally less secure in doing so, all in the name of bringing you clickable profiles within an email address, like so:

Man in the Middle:
Here's the problem. What LinkedIn does is redirect all email you receive across its own IMAP servers, as shown below.

The company is at least up-front about this, writing: "Normally your device connects directly to the servers of your email provider (Gmail, Yahoo, AOL, etc.), but we can configure the device to connect to the Intro proxy server instead."
Note that this isn't just a service for LinkedIn users communicating over LinkedIn's proprietary email service. If it was, there wouldn't be so much of a problem. The idea here is that LinkedIn can cross-reference and inject profile information about people communicating with you who also happen to have LinkedIn profiles. The company explains a little more in the same post, writing: "The Intro proxy server speaks the IMAP protocol just like an email provider, but it doesn’t store messages itself. Instead, it forwards requests from the device to your email provider, and forwards responses from the email provider back to the device. En route, it inserts Intro information at the beginning of each message body — we call this the top bar."
What LinkedIn is describing here is a classic man-in-the-middle attack in which an organization intercepts data between Points A and B by secretly positioning itself to snoop on the data stream. Granted, LinkedIn isn't doing this in secret -- but that's still the fundamental security flaw. If you use your email for anything remotely confidential, LInkedIn is now sitting in a position to retain a copy. And since their own server is now the pass-through point for your authentication credentials and security data, you're going to have a hard time keeping anything private.
A blog post at Bishop Fox goes on to detail the problems with this program, which are legion. You're changing the cryptographic signature of your own email (or allowing LinkedIn) to change it, you're connecting to a third-party to provide a vital link in a service, LinkedIn is making changes to the way your iPhone operates that could be exploited to compromise its security at a later date, the company's privacy policy is vague, it's already under investigation for spamming address books and lifting data out of other email providers without permission, and the company had 6.5 million passwords stolen last year. (LinkedIn denies the allegation).
Belatedly, the company appears to have realized it might as well have hung a sign over the door reading: "Welcome NSA, Hackers, Ne'er Do-Wells!" It has since pledged to respect its own privacy policy, made vague comments about creating a new Mail profile on the iPhone but left old profiles unaffected (as though this would impact the fact that your mail was still being fed through the proxy service) and pledges really, really, good security. Like, totally the best.
This is a terrible idea. Do not sign up for an email service with a company that already engages in shady "recruitment" tactics and scans open browser windows without your consent. Don't trust the security of a company with massive password breach issues. And don't tell corporate IT that you think this sounds like a fine and dandy idea unless you're trying to make your Sysadmin drop dead of a coronary.

