Ubuntu Privilege Escalation Security Flaw Puts Millions Of Linux Users At Risk
When operating systems are installed by default, users and programs are given a set of permissions that allow them to do certain tasks within the operating system's confines. On Linux, root permissions grant the highest level of access to the system and are typically the end goal for attackers and malware on a system. While some programs need root permissions to complete tasks, most users and programs do not and are assigned lower-level permissions. However, bugs within the programs with higher-level permissions could allow a lower-level user to run code or gain access to data at that higher level, which is where privilege escalation comes into play.
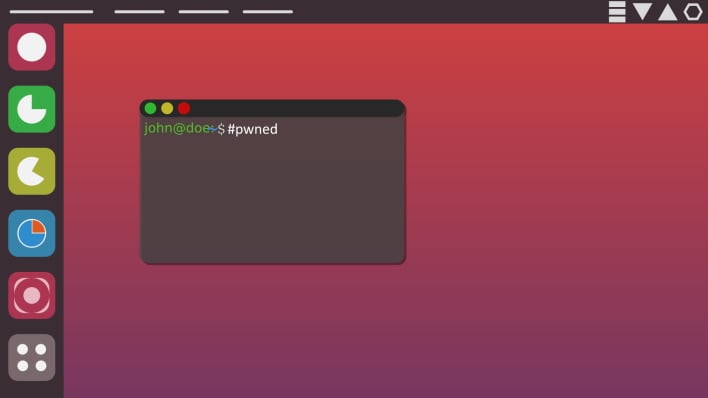
In this case, the Qualys Research Team discovered several vulnerabilities within the snap-confine tool on Linux operating systems such as Ubuntu. However, if exploited, one such vulnerability (CVE-2021-44731) would allow "any unprivileged user to gain root privileges on the vulnerable host." The Qualys team was subsequently able to develop an exploit for the vulnerability and "obtain full root privileges on default installations of Ubuntu." While there is a more technical explanation of how this works, you can see what this simple exploit looks like on a previously fully patched version of Ubuntu above.
Though there is no exploit or proof-of-concept out there, the information surrounding this vulnerability is, and it is quite likely a threat actor is working on it. As such, it is recommended that security teams and end-users running Linux distros with snap-confine apply patches for these vulnerabilities as soon as possible. However, it should be noted that as long as a threat actor cannot get onto your system as a low-privileged user, there is nothing to worry about. In any event, it is always good to stay up to date with operating systems, as you never know what could be lurking out there in older unpatched versions.

