Not everything has to be high-tech to perform dastardly deeds these days, and the same is true of
malware. However, malware can slip by conventional
security solutions using some email tricks and social engineering and still infect end-users, as
Microsoft reports.
This Tuesday, the Microsoft Security Intelligence
reported on Twitter that several “active email campaigns that use BazarLoader to deliver a wide range of payloads” are being tracked. These campaigns have been found to use some interesting techniques to get around what Microsoft describes as “conventional email security solutions and best practices.”
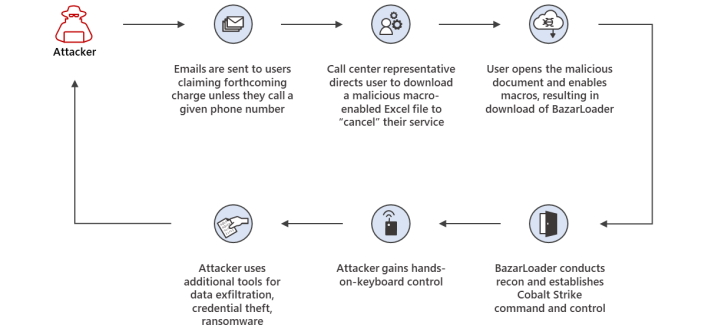
The first reported campaign is called “BazaCall,” which uses phone numbers rather than a malicious link. Users then call the number and are tricked into downloading the BazarLoader through a malicious macro-enabled Excel file. Once this file is opened, BazarLoader installs its payload, which in this case is Cobalt Strike, giving the attacker hands-on control.
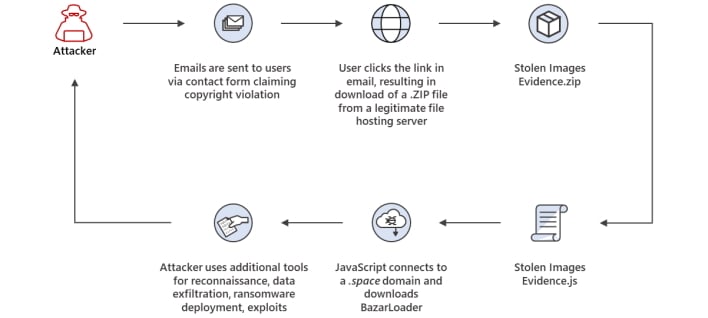
Another campaign hides under the guise of the DMCA wherein users are sent an email claiming copyright violation with “stolen images.” When a user clicks a link in the email, a ZIP folder is downloaded that contains a javascript file which, when opened, downloads BazarLoader. Again, a payload is installed, and the attacker gains access to the machine.
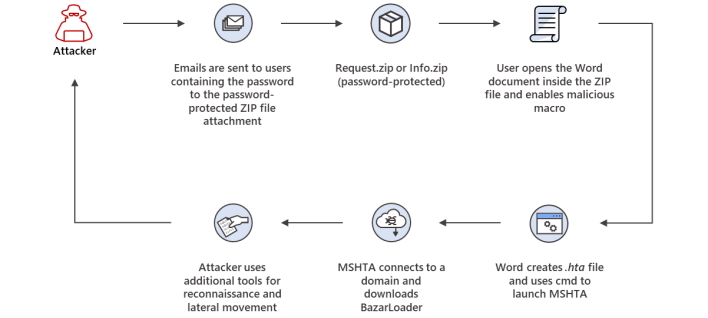
The third and final campaign that Microsoft reported uses “compromised accounts to hijack email threads and attach a Word document in a password-protected ZIP file.” Once the document is opened, macros within it lead to the download of BazarLoader that once again downloads and installs a payload.
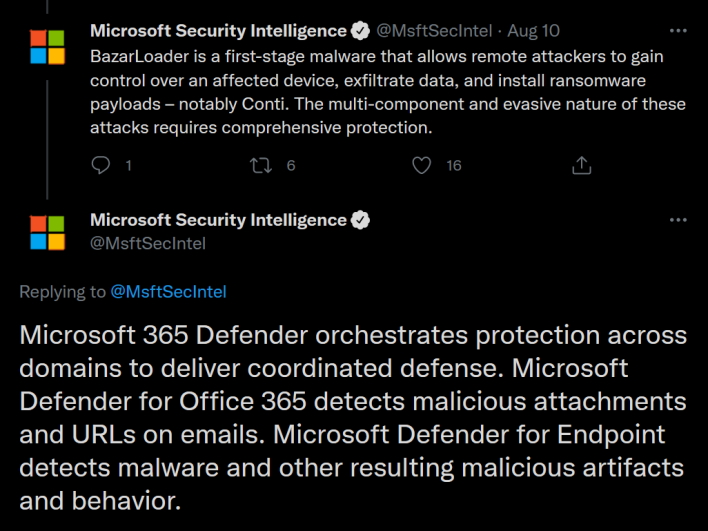
One common thread between these campaigns is BazarLoader, which Microsoft explains is a “first-stage malware that allows remote attackers to gain control over an affected device, exfiltrate data, and install ransomware payloads – notably
Conti.” However, Microsoft 365 Defender will reportedly catch the malicious attachments and URLs while “Microsoft Defender for Endpoint detects malware and other resulting malicious artifacts and behavior.”
Though Microsoft Defender may be a good solution, end-user training is also critical in defending against malware campaigns. For example, if people did not click random links and fact-checked phone numbers or information contained in emails to ensure legitimacy, there would be less of an issue with this. Hopefully, as time goes on, people will wise up to even the simplest of tricks.