Marriott Hotel Duped By Social Engineering In An Embarrassing 20GB Data Breach

Last month, a ransomware gang known as ALPHV struck The Allison Inn & Spa, stealing employee and customer data. ALPHV then published this information to the open web, where it could be indexed by search engines and viewed without the use of the Tor network. While the website that presented the data for download wasn’t up for very long, it’s likely that someone downloaded the data while the website was live and will post it to somewhere like Breach Forums for cybercriminals to download.
However, customers and employees of The Allison aren’t alone in having their data stolen from a vacation destination. A Marriott hotel has suffered a similar data breach at the hands of an unknown group. Marriott has been the victim of multiple data breaches in the past, including a 2020 breach involving the personal information of 5.2 million guests, as well as a 2014 breach that wasn’t discovered and reported until 2018, resulting in multiple class action lawsuits and a fine by the UK government.
Unlike the breach affecting customers and employees of The Allison, this new Marriott breach doesn’t seem to have been carried out by a ransomware gang. While ransomware groups often engage in double extortion by both encrypting the data on victims’ computers and threatening to post the data online unencrypted, other extortion groups operate by simply exfiltrating data from victims’ computers and threatening to post it online. An extortion group by the name of RansomHouse recently threatened to release 450GB of AMD data, and no ransomware seems to have been involved.
However, customers and employees of The Allison aren’t alone in having their data stolen from a vacation destination. A Marriott hotel has suffered a similar data breach at the hands of an unknown group. Marriott has been the victim of multiple data breaches in the past, including a 2020 breach involving the personal information of 5.2 million guests, as well as a 2014 breach that wasn’t discovered and reported until 2018, resulting in multiple class action lawsuits and a fine by the UK government.
Unlike the breach affecting customers and employees of The Allison, this new Marriott breach doesn’t seem to have been carried out by a ransomware gang. While ransomware groups often engage in double extortion by both encrypting the data on victims’ computers and threatening to post the data online unencrypted, other extortion groups operate by simply exfiltrating data from victims’ computers and threatening to post it online. An extortion group by the name of RansomHouse recently threatened to release 450GB of AMD data, and no ransomware seems to have been involved.
The group behind the most recent Marriott breach reached out to DataBreaches.net to share details about the incident, but didn’t provide a name for itself. This nameless extortion group claims to have been active for roughly five years, avoiding media coverage by negotiating with victims in a discrete and confidential manner. The group also says that it doesn’t ever encrypt victim data so as to not disrupt business operations. However, the group has apparently come out of the shadows and revealed its involvement in this latest data breach because the group intends to change its mode of operation.
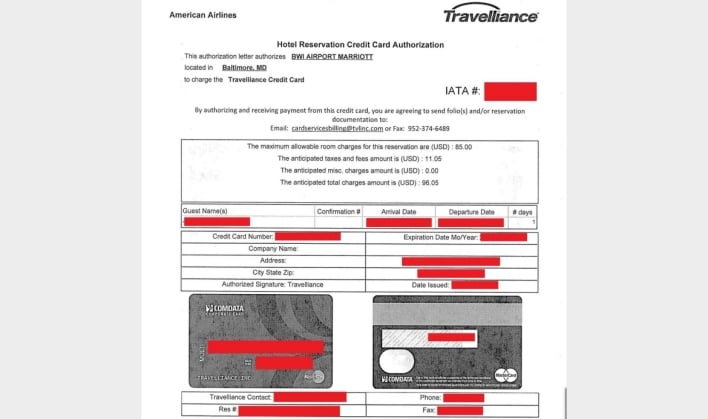
Files shared by the nameless extortion group show that the data breach affected the BWI Airport Marriott in Maryland. The stolen files contain guest information relating to arrangements made by airlines, including flight crews’ arriving and departing flights, names, room numbers, and corporate credit card numbers, CVVs, and expiration dates. he extortion group claims to have stolen 20GB of data in total. Marriott has acknowledged the breach and provided its side of the story as well.
According to Marriott, the extortion group used social engineering tactics to trick a Marriott associate into giving the group access to his computer. The hotel says that the breach was limited to this single associate’s computer and that the breach was contained within six hours. The extortion group didn’t dispute these details.
Some time after Marriott began investigating the breach, the extortion group contacted the hotel in the hopes of negotiating payment. Both parties indicated that no money exchanged hands, though the group claims that the hotel was open to communication at first, then suddenly went silent. Marriott maintains that most of the stolen data is composed of “non-sensitive internal business files,” but stated that law enforcement is assisting in the investigation and that the hotel will be sending notices to around 300-400 people.
Files shared by the nameless extortion group show that the data breach affected the BWI Airport Marriott in Maryland. The stolen files contain guest information relating to arrangements made by airlines, including flight crews’ arriving and departing flights, names, room numbers, and corporate credit card numbers, CVVs, and expiration dates. he extortion group claims to have stolen 20GB of data in total. Marriott has acknowledged the breach and provided its side of the story as well.
According to Marriott, the extortion group used social engineering tactics to trick a Marriott associate into giving the group access to his computer. The hotel says that the breach was limited to this single associate’s computer and that the breach was contained within six hours. The extortion group didn’t dispute these details.
Some time after Marriott began investigating the breach, the extortion group contacted the hotel in the hopes of negotiating payment. Both parties indicated that no money exchanged hands, though the group claims that the hotel was open to communication at first, then suddenly went silent. Marriott maintains that most of the stolen data is composed of “non-sensitive internal business files,” but stated that law enforcement is assisting in the investigation and that the hotel will be sending notices to around 300-400 people.

