Microsoft Blames Government Stockpiling Of OS Exploits For Global WannaCrypt Outbreak
Last Friday, we reported on a major cyberattack involving ransomeware that hit a large number of computers - including some belonging to the UK's National Health Service. At first, the malware's reach wasn't too clear, but as the weekend went on, we learned that the number of affected PCs reached at least 200,000 worldwide. Given the nature of this beast, that is downright terrifying.
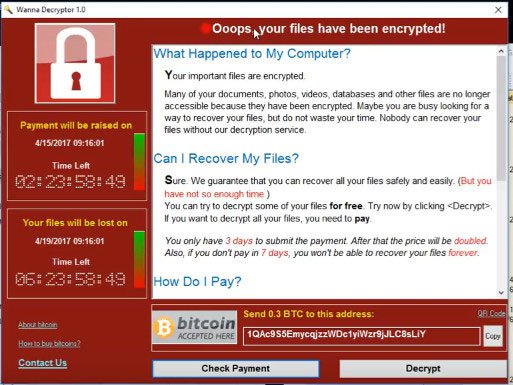
The big question right now is, "Who's at fault?" The blame could easily be shifted to Microsoft, as the bug that allowed this to happen was directly attributed to its own code. While the company is to be commended for releasing a rare Windows XP patch to help squash the bug, it comes a bit too late. Microsoft knew about this vulnerability since at least March, and given that it seems a huge number of affected PCs were running outdated versions of Windows, the company could have been proactive and issued an emergency patch before it was too late.
Microsoft, however, is placing the blame on the US government and its National Security Agency. While the bug existed in Windows, the tool was developed in-house at the NSA, and then stockpiled along with a trove of other exploits. The NSA knew about the potential of this exploit long before Microsoft or the public did, but chose to keep it close to its chest rather than report it. The NSA clearly didn't want the bug fixed; it wanted to exploit it.

Windows XP received a belated patch to defend against Wanna Decrypter
Some might believe that it'd be a-OK for the NSA to store these exploits as long as they don't make their way out of the agency, but this debacle was the direct result of a leak. The NSA might boast about its defenses, but the fact of the matter is, we've seen exploits and documents trickle out of the agency on multiple occasions.
Microsoft President and Chief Legal Officer Brad Smith likens an exploit like Wanna Decrypter leaking out to the US military having some of its Tomahawk missiles stolen. If that sounds outlandish, ponder the fact that a staggering 200,000 computers have been infected with malware that demands $300 worth of Bitcoin to clear; otherwise, data is gone. It wasn't only user PCs affected here, it was hospitals. If the NSA hadn't developed a tool to exploit the issue, or had notified Microsoft of the issue when it was first discovered, those 200,000 (and counting) PCs wouldn't have been compromised.
In the span of just a few short days, we've really received our biggest wake-up call ever that computer security today is not where it needs to be.

