Microsoft Security Research Details SolarWinds Solorigate Elaborate Second Stage Backdoor Attack

The SolarWinds breach and subsequent attacks are shaping up to be the most elaborate and long-lasting attacks in some time. Microsoft has done a deep dive into the second stage of the attacks and has found that the attackers are both skilled and elusive. Overall, though, the deep-dive gives us a look into what transpired to make these attacks tick, and it is rather interesting.
Once on a network through the Solorigate backdoor (SUNBURST), getting anything done requires new malicious software and a level of secrecy that can be difficult to maintain. Moreover, when executing an attack, you do not want to burn the entire bridge if discovered on a network. Thus, the SolarWinds hackers attempted to separate their backdoor and the tools they used to collect and send data. You can see the extreme separation in the chart Microsoft created below.
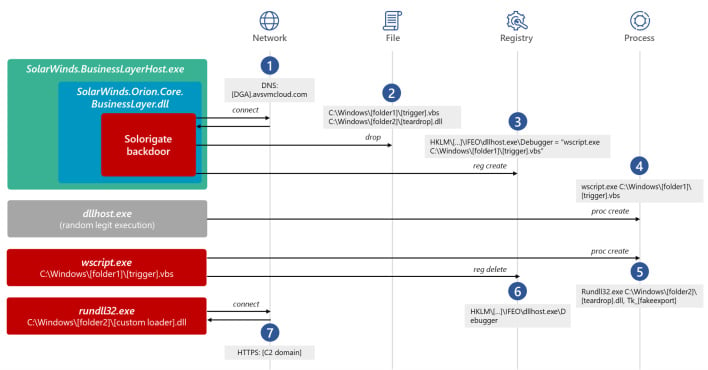
Ultimately, the hackers use Cobalt Strike, which is somewhat of a 'Swiss Army Knife' of hacking tools that were initially tools for the good cybersecurity folks. To get this toolkit onto a network, the hackers wrapped it in other second-stage malware, such as TEARDROP or Raindrop, among others. These malicious programs, including Cobalt Strike assets, attempted to disguise themselves as legitimate Windows processes to blend-in while executing malicious tasks. What's more is that the attackers, once on a network, disabled some event logging and changed firewall rules to keep their profile quiet and stealthy.
In total, as Microsoft explains, "As we continue to gain deeper understanding of the Solorigate attack, we get a clearer picture of the skill level of the attackers and the extent of planning they put into pulling off one of the most sophisticated attacks in recent history." The sheer level of complexity, planning, and execution make for an impressively concerning attack. However, this is not kudos to the hackers but a security warning to companies and organizations at risk. Furthermore, Microsoft's information can be crucial for stopping attacks like this in their future tracks.

