Microsoft Rushes Out Mandatory Windows Patches For PrintNightmare Exploit, Update ASAP

As if fussing with a printer is not maddening enough, a recent Windows Print Spooler exploit called 'PrintNightmare' left users vulnerable to remote code execution attacks. Not cool. Fortunately, Microsoft has made rather quick work of rolling out an out-of-band patch, which is being sent out via Windows Update (or you can grab it manually).
Out-of-band patches for Windows are somewhat on the rare side, though they do happen on occasion. Normally, Microsoft packages up cumulative updates and dishes them out on the second Tuesday of every month, otherwise known as Patch Tuesday. Sometimes, however, problems or exploits arise that simply can't wait.
This is one of them. Published as CVE-2021-34527, Microsoft warned that an attacker could leverage the exploit to run arbitrary code on a victim's PC and perform "privileged file operations." As such, an attacker could then install programs, such as malware, or muck with data (view, change, or even delete) and create new accounts with full system rights.
Initially, Microsoft only offered up a couple of workarounds. This left IT admins with a choice of disabling the print spooler entirely, which would prevent people from being able to print locally or remotely (not ideal, obviously), or disable inbound remote printing through a Group Policy update. However, Microsoft has found the issue and patched out the bug.
"Microsoft has completed the investigation and has released security updates to address this vulnerability...We recommend that you install these updates immediately," Microsoft says.
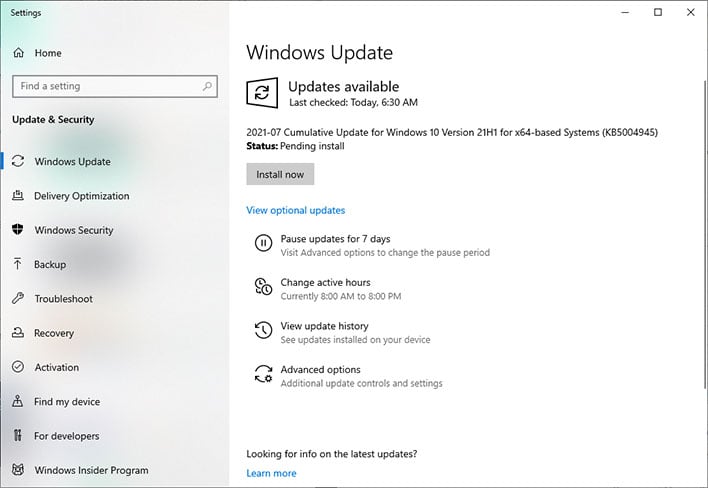
The easiest way to kick this exploit to the curb is to fire up Windows Update, where the patch is being rolled out to various Windows builds automatically—the precise KB designation will vary depending on which version of Windows you are running, with KB5004945 (as shown above) being one of them (others include KB5004946, KB5004947, KB5004950, KB5004951, KB5004953, KB5004958, and KB5004959).
Alternatively, you can head to Microsoft's Update Catalog and download the appropriate patch for your version of Windows, for a manual installation.
"After installing this and later Windows updates, users who are not administrators can only install signed print drivers to a print server. By default, administrators can install signed and unsigned printer drivers to a print server. The installed root certificates in the system’s Trusted Root Certification Authorities trusts signed drivers," Microsoft explains.
It's not clear if attackers are aggressively pursuing this exploit in the wild. Regardless, it's a good idea to patch up your Windows PC sooner than later, to play it safe.