Microsoft Patches DogWalk Zero-Day Flaw That Cruised Past Windows Defenses

Microsoft has finally released a security update that addresses a zero-day vulnerability that went unpatched for more than two years. The vulnerability, known as DogWalk, appears in the national vulnerability index as CVE-2022-34713. Microsoft has assigned the vulnerability a high severity rating of 7.8. The company’s security advisory confirms that the vulnerability has been exploited in the wild, prompting the US Cybersecurity and Infrastructure Security Agency (CISA) to add the vulnerability to its known exploited vulnerabilities catalog and require federal agencies under its jurisdiction to apply Microsoft’s patch by August 30th.
The DogWalk vulnerability was first discovered and reported to Microsoft near the end of 2019 by security researcher Imre Rad. However, at the time, Microsoft didn’t consider the researcher’s findings to be indicative of a vulnerability that needed patching. However, Microsoft later changed its tune after further exploits of the vulnerability became known. The vulnerability in question exists in the Microsoft Support Diagnostic Tool (MSDT). This tool can receive further diagnostic instructions by loading files with the .diagcab file extension. As a security measure, MSDT won’t execute .diagcab packages unless they have been signed with a valid code signing certificate.
The DogWalk vulnerability was first discovered and reported to Microsoft near the end of 2019 by security researcher Imre Rad. However, at the time, Microsoft didn’t consider the researcher’s findings to be indicative of a vulnerability that needed patching. However, Microsoft later changed its tune after further exploits of the vulnerability became known. The vulnerability in question exists in the Microsoft Support Diagnostic Tool (MSDT). This tool can receive further diagnostic instructions by loading files with the .diagcab file extension. As a security measure, MSDT won’t execute .diagcab packages unless they have been signed with a valid code signing certificate.
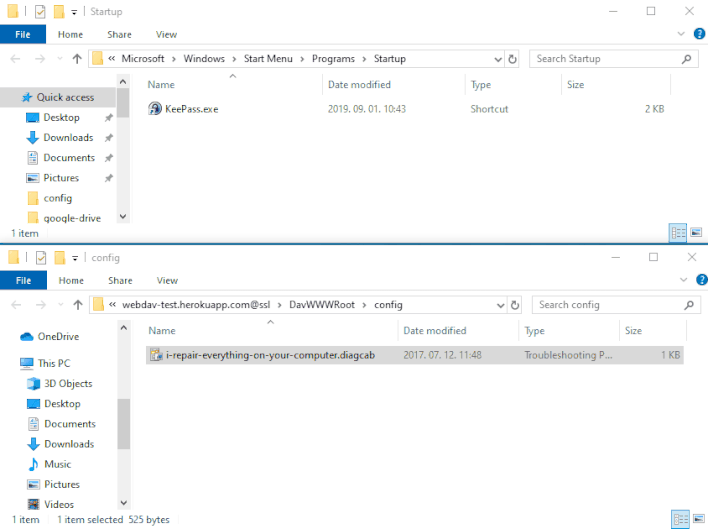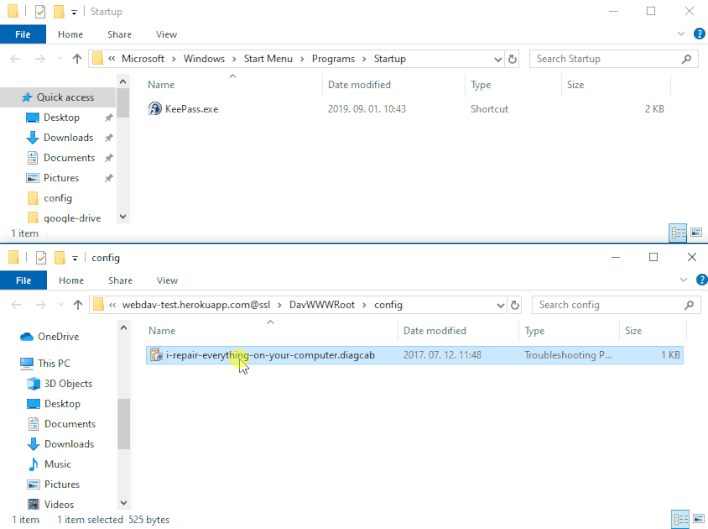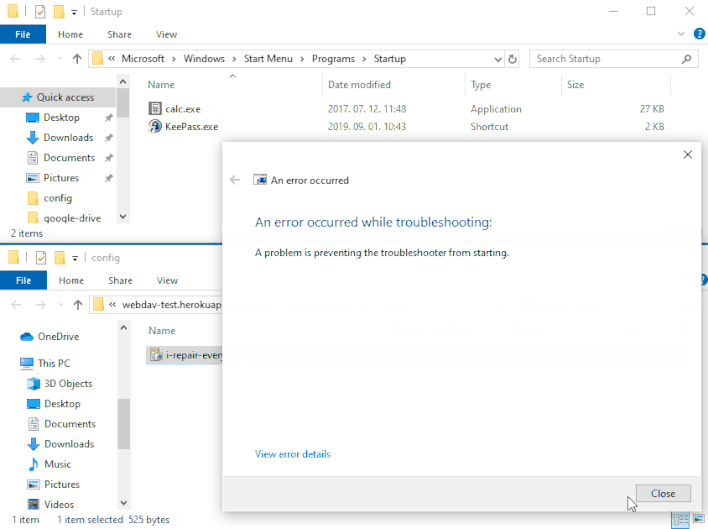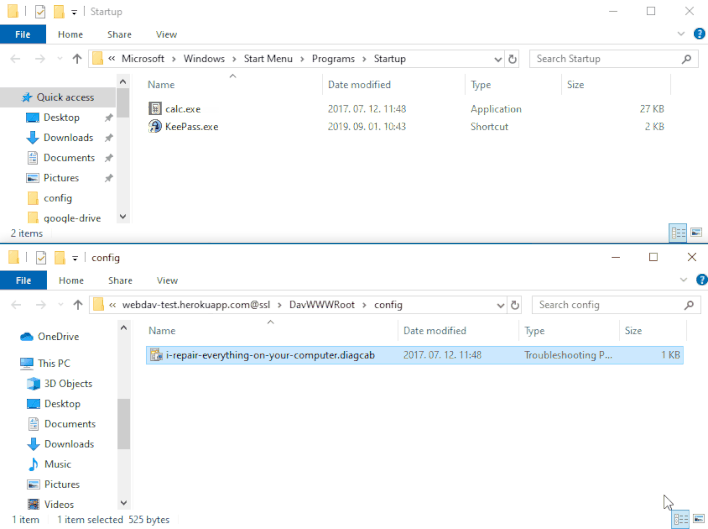
However, Imre Rad discovered that when initially opened by MSDT, .diagcab packages can save any file to any location on a machine. This occurs before MSDT performs the signature check to decide whether to execute the package. As shown in the demonstration above, a threat actor can exploit this behavior by distributing a .diagcab package that places a malicious executable in the Windows Startup folder. Once this malicious executable is in place, Windows will automatically run the executable upon next startup. This vulnerability allows an attacker to bypass Windows’ signature verification check by tricking unsuspecting victims into double-clicking on a .diagcab file, usually through social engineering.
Windows users should install Microsoft’s August 9th Patch Tuesday update to address this vulnerability.
Top Image Credit: Johann on Pexels
Windows users should install Microsoft’s August 9th Patch Tuesday update to address this vulnerability.
Top Image Credit: Johann on Pexels

