Microsoft PrintNightmare Hack Grants Windows Admin Privileges In Latest Security Facepalm

Earlier in July, the PrintNightmare vulnerability was discovered, wherein a threat actor could exploit the vulnerability to gain system-level access to a device. This was only speculation at first, but that has now changed, as cybersecurity researcher Benjamin Delpy has shown.
Since the discovery of PrintNightmare, Delpy has been working to both investigate and exploit it for research purposes. Initially, he reported that he could achieve both remote code execution and local privilege escalation using PrintNightmare on a fully patched server with “Point & Print” enabled. Following that development, Delpy was more recently able to create a web-hosted printer that leveraged the vulnerability on any PC that connected to it.
What came from this was the ability to upgrade any user on any vulnerable PC to a SYSTEM user. All it takes is adding the printer as if it were any other device, and then you have SYSTEM privileges. According to Delpy, who spoke with BleepingComputer, it is possible that Russian threat actors are abusing his print servers, and it likely will not be long before they have their version of the system. In any event, you can see how this exploit works in the Twitter post up above.Little #printnightmare (ep 4.3) upgrade : user-to-system as a service🥝
— 🥝 Benjamin Delpy (@gentilkiwi) July 27, 2021
> Open SYSTEM prompt
connect to \\printnightmare[.]gentilkiwi[.]com (remove [ ]) with
- user: .\gentilguest
- password: password
Open 'Kiwi Legit Printer - x64', enjoy SYSTEM
(just one printer this time🤪) pic.twitter.com/XJiF0szm4p
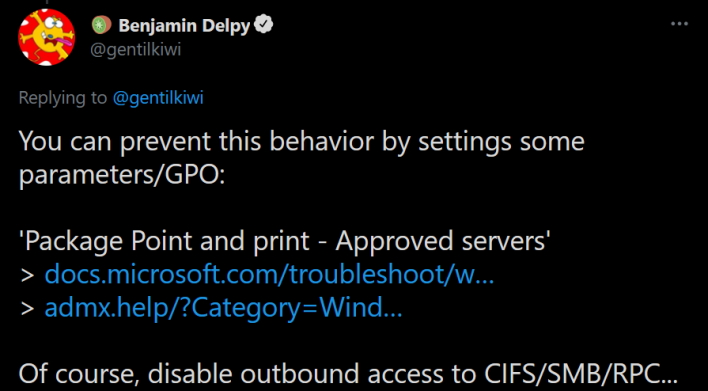
As far as individuals go, do not install random printers, and disable the same services by following Microsoft tutorials such as this one for SMB. Outside of this, until Microsoft provides a proper fix, PrintNightmare mitigation is quite difficult. Therefore, we hope that Delpy’s demonstration pressures Microsoft to get moving with a fix, as this recurring nightmare will only continue.