Microsoft CodeQL Tools Goes Open Source To Aid Firms With Solorigate Threat Analysis

Now that Microsoft’s investigation into the Solorigate hack has concluded, it is time to pick up the pieces and plot a [secure] path forward. In doing this, Microsoft has internally utilized several tools, including CodeQL, to hunt for Solorigate activity. Microsoft, however, “believes in leading with transparency and sharing intelligence with the community for the betterment of security practices and posture across the industry as a whole,” and is subsequently sharing its tools to help other companies in hunting Solorigate.
According to Microsoft’s blog post, CodeQL is “a powerful semantic code analysis engine” which works by a two-pronged approach. When code is compiled, CodeQL builds a database that grabs a model of that code. Once the database is constructed, one can query it like a regular database but with complex code conditions as the query.
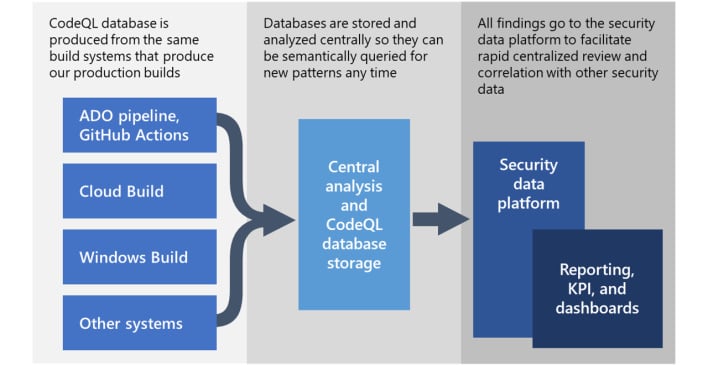
Ultimately, while CodeQL can be used for other vulnerability hunting, the new Solorigate queries Microsoft authored will hopefully help the thousands of companies affected by the hack. If you believe you need to use CodeQL, you can find out more about Microsoft’s contributions at the GitHub page for CodeQL and start threat hunting today.

