Shady Malware Distributor Is Hunting Minecraft Players With Chaos Ransomware

Minecraft, owned by Microsoft, has become one of the most popular games in the last 12 years. However, with this level of popularity comes numerous issues, such as cheating across the 22 platforms on which Minecraft is offered. Thankfully, many of these cheaters eventually get caught and banned, but there are also ways around a ban to continue wreaking havoc on servers worldwide. This includes users going out and acquiring alternative or "alt" accounts, sometimes for nefarious activities.

When it comes to using alt-accounts for nefarious activities, people are generally not willing to pay when they know that the account will eventually get banned as well. As such, these people go online and look for lists of stolen accounts that can be used and thrown away if banned. Understanding this premise, Fortinet discovered that threat actors have disguised Chaos ransomware as a text-file list of "Minecraft Alt" accounts. That file gets downloaded and opened under the guise that it is a handy list of stolen accounts, which is where the problem lies.
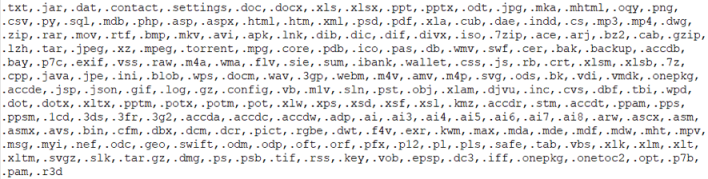
Once opened, the executable encrypts files smaller than ~2MB and effectively deletes anything larger with specified extensions by filling the data with random bytes. Moreover, the ransomware deletes shadow copies from the machine, disallowing any recovery of files that had become encrypted. After this series of events unfolds, a readme.txt file is dropped on the victim's device, asking the user to pay 2,000 yen or around $17. Though the program's code does not indicate the origin, the request of yen and the ransom note only being available in Japanese points to a Japanese threat actor targeting Japanese Minecraft players on Windows devices.
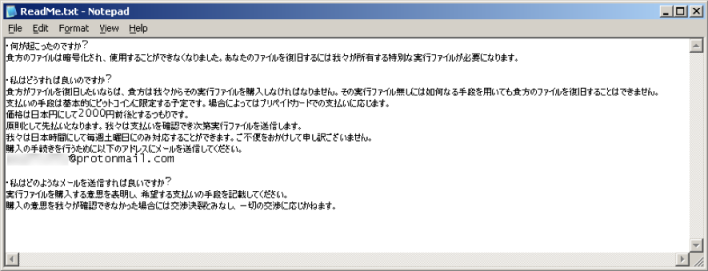
The Fortinet team elaborates, "despite its cheap ransom demand, its ability to destroy data and render it unrecoverable makes it more than a mere prank to annoy Japanese Minecraft gamers." Of course, the solution to this problem is to not go looking for Minecraft cheats and alt accounts in the first place, but getting hit this hard with ransomware is quite severe. Let us know what you think in the comments below.

