Millions Of Wi-Fi Routers Could Be Enslaved In Nasty Mirai Botnet, Check Your Model Here

Earlier in the month, Tenable security researchers discovered a vulnerability allowing attackers to bypass authentication on millions of routers from 17 different vendors. However, it now appears that threat actors are actively exploiting this to deploy malicious Mirai botnet payloads.
Evan Grant of Tenable published research on August 3rd that determined anyone could bypass authentication on devices manufactured by Arcadyan. In short, the problem stems from the router’s handling of URLs, in that it stops checking for bypass attempts as soon as it finds a piece of the URL within a bypass or white- list.
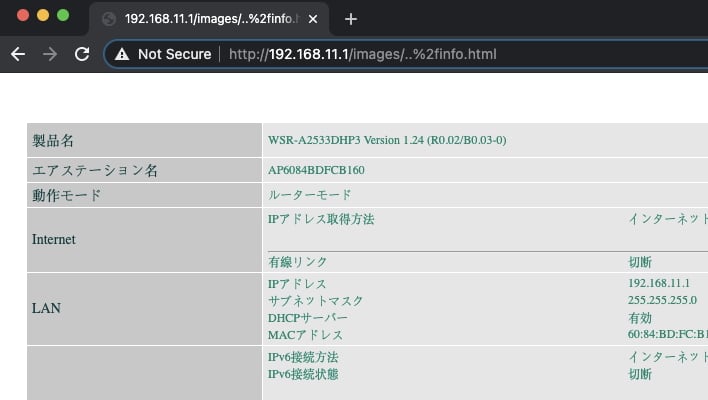
Using Grant’s example, if you wanted to navigate to http://router/images/someimage.png, it would load this normally because /images/ is in the bypass_list. However, with some tinkering, you can append /info.html or any page to the URL so long as a bypass list option comes earlier in the URL. Then, you can get access to pages that would typically require authentication.
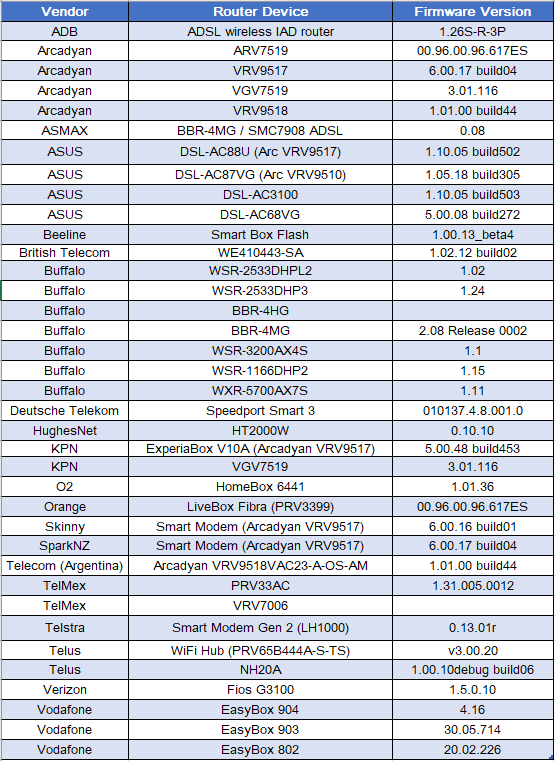
Just a few days later, Juniper Networks security researchers Mounir Hahad and Alex Burt “identified some attack patterns that attempt to exploit this vulnerability in the wild coming from an IP address located in Wuhan, Hubei province, China.” These active exploitation attempts appeared to try and deploy a Mirai botnet variant on the vulnerable routers that we have listed below, courtesy of Tenable.