Google Warns Of Sneaky Social Engineering Hack From North Korea Targeting Security Researchers

Security researchers beware, as Google is reporting that a “government-backed entity based in North Korea” is targeting anyone working on vulnerability research and development. These attackers use several different accounts and means of communication to reach out to a target. Then, they share that they have a 0-day available for research, but it is instead just a trap ending in a compromised device.
In a report published yesterday, the Google Threat Analysis Group (TAG) announced this dangerous situation that is still developing. To build credibility, the attackers created several different Twitter accounts for interacting with people and posting blog links, videos, and retweeting seemingly legitimate posts from accounts they own. The blog posts that were created and shared on Twitter are simple vulnerabilities that have already been disclosed or are “guest” posts from “unwitting legitimate security researchers, likely in an attempt to build additional credibility with other security researchers.”
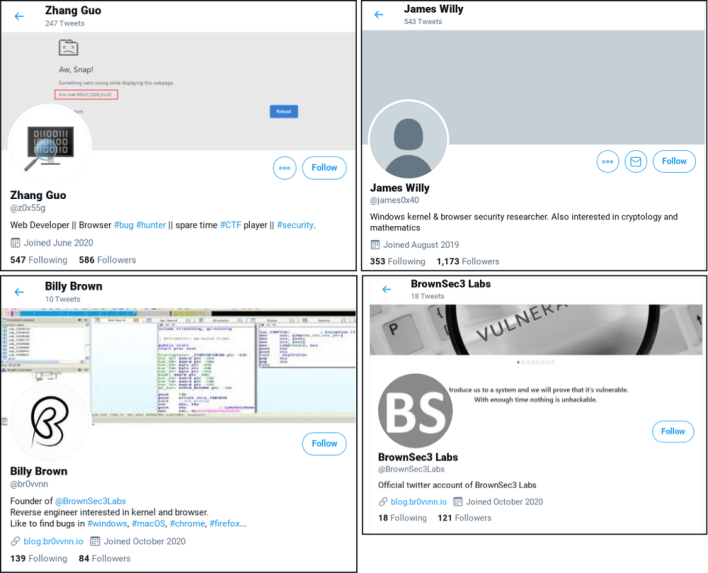
While “building credibility,” the fake accounts reach out to security researchers, offering collaboration on a project together. Using many different platforms, such as Twitter, LinkedIn, Telegram, Discord, Keybase, and email, the attackers send a Visual Studio Project, which contains a malicious DLL file that immediately connects to command-and-control domains.
Besides this attack method, it also appears that the fake researchers’ blog performs a “drive-by download,” which compromises the legitimate researcher. It seems many people were affected by this, from smaller researchers to the owner of Hyperion Gray, a security research company. The owner, Alejandro Caceres, is now offering $80k for full details on the attacker after making it his mission to end the shenanigans.
he goes by the name James0x40 on twitter (now banned), @kw0dem on telegram, gmail is kvlpmap@gmail.com, and djokovic808 (maybe a tennis fan!?). Anyway, yes I was hacked. No, no customer information was leaked, this was on a private VM for this exact reason. Anyway I'm offering
— Alejandro Caceres (@_hyp3ri0n) January 26, 2021
make it 80k, i'll match chef.
— Alejandro Caceres (@_hyp3ri0n) January 26, 2021
Overall, this sort of attack is incredibly concerning as the details of the malware sent are not known. The attack generally occurred on patched and up-to-date versions of Windows 10 and Chrome browser, so what the attackers have is brand new. If you are a security researcher, keep your head on a swivel and make sure that you vet any contacts before taking files. You never know where those files come from or what is buried inside of them.
(Now Defunct Twitter account images courtesy of Google)

