An Old NSA-Found Security Threat Is Still Menacing Windows Users And Data Centers

The vulnerability, tracked as CVE-2022-34689, has a Common Vulnerability Scoring System (CVSS) score of 7.5, thanks to various metrics. While this score is not wholly indicative of the dangers of this vulnerability, it is a basis for concern. Namely, if exploited, this vulnerability could allow an attacker to pose as a legitimate entity with valid certificates used in code signing or verification.
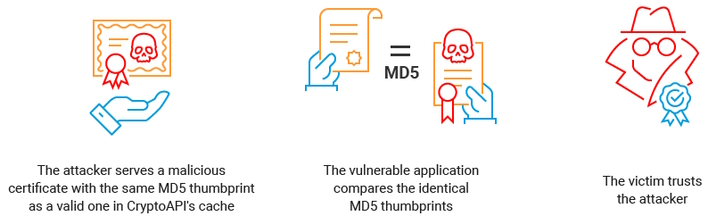
Akamai, the team behind the newly published research and proof-of-concept exploit code for CVE-2022-34689, reports that an attacker could mask their identity and bypass various security protections. This is thanks to a change in the crypt32.dll with the singular function “CreateChainContextFromPathGraph,” wherein lies a check to see if a certificate is already in the cache and subsequently verified. Before a patch fixed the vulnerability, this check would use an MD5 thumbprint of the received certificate and compare that against those in the cache.
It was theorized that, given long-standing collision problems with MD5, it would be possible to serve a certificate whose thumbprint matches one in the cache. Now, the Akamai team has proven this with proof-of-concept code that bypassed one check and made Windows believe the malicious certificate was a trusted one.
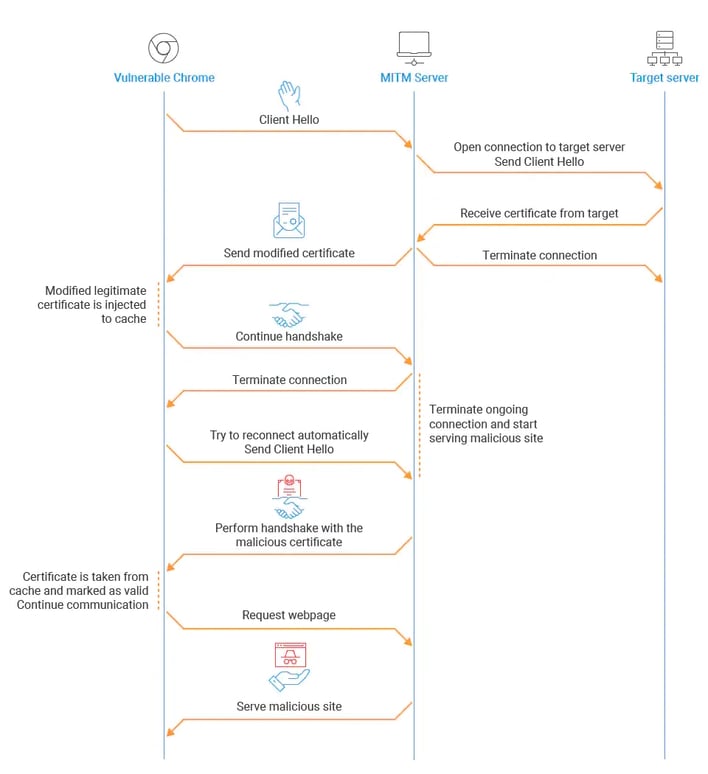
Per the report, a lot of code that uses the CryptoAPI could be exposed to this vulnerability which could require patches for even discontinued versions of Windows, such as Windows 7. Further, it is noted that “fewer than 1% of visible devices in data centers are patched, rendering the rest unprotected from exploitation of this vulnerability.” However, this is not quite as scary as it first seems, as there is a limited scope of vulnerable applications and Windows components that meet the criteria for exploitation.
In any event, research is ongoing into the vulnerability, but it is not expected to be anything like the CurveBall vulnerability, which the NSA also discovered. This does not mean you should not update your systems, though, as vulnerabilities like this will continue to come back and haunt us if not properly addressed.

