CapraRAT Malware Targets Android Users By Spoofing YouTube, What You Need To Know

The Transparent Tribe is believed to be a Pakistani group or actor that is targeting both military and diplomatic individuals in Pakistan as well as India. The goal of the threat actor(s) is to spear-phish targets “privy to affairs involving the disputed region of Kashmir, as well as human rights activists working on matters related to Pakistan,” according to the SentinelLABS report. In this endeavor, the group has employed CapraRAT, an Android RAT that is disguised as a legitimate application.
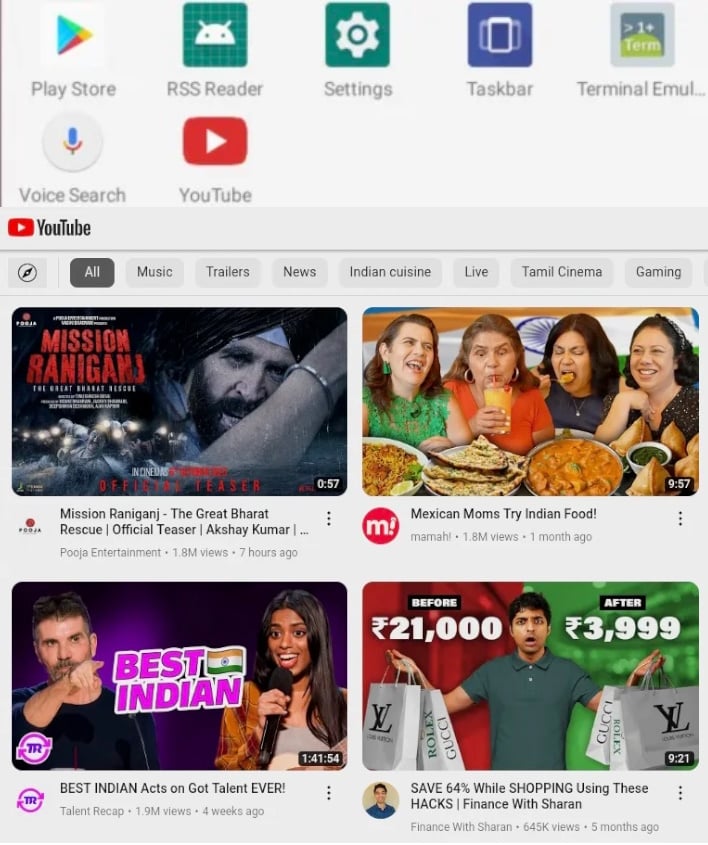
Previously, CapraRAT was disguised as a dating service that was hosted on Transparent Tribe websites, utilizing social engineering techniques to get users to download the malware. Now, though, it appears that CapraRAT is disguising itself as the YouTube app wholesale or spoofing an app for a YouTube channel belonging to Piya Sharma. This latter version of CapraRAT indicates to the SentinelLABS team that “the actor continues to use romance-based social engineering techniques to convince targets to install the applications, and that Piya Sharma is a related persona.”
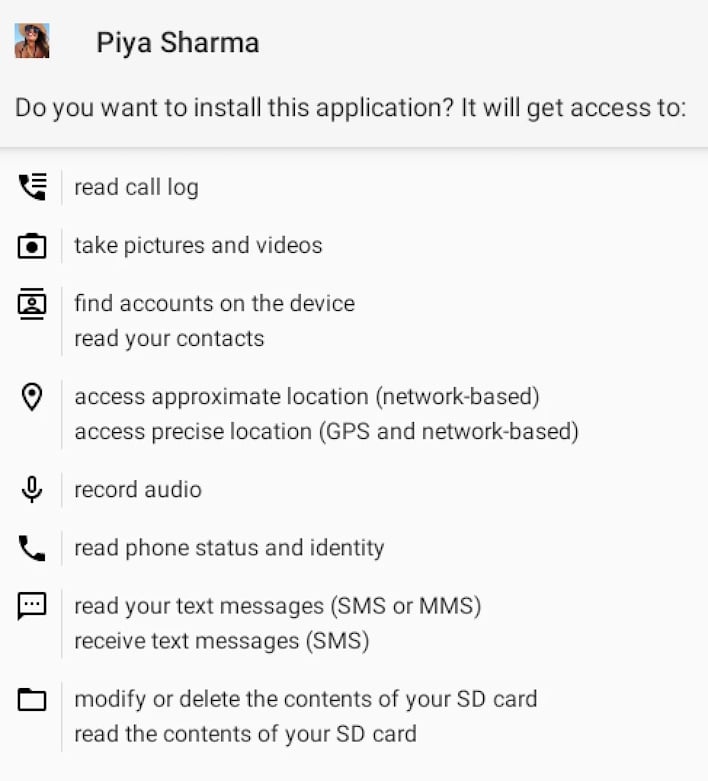
Regardless of how CapraRAT might get onto your device, it is rather spooky if it does manage to get installed. The researchers note that CapraRAT can record with the microphone or any camera, collect or send SMS and MMS messages, read call logs or initiate phone calls, take screenshots, override system settings, and modify files on the phone. Any collected data is then sent off to the Transparent Tribe command-and-control (C2) servers, which have been associated with the group for some time.
With this information in mind, SentinelLABS recommends, "Individuals and organizations connected to diplomatic, military, or activist matters in the India and Pakistan regions should evaluate defense against this actor and threat.” However, this is also a good opportunity for everyone in the Android ecosystem to know that threat actors are leveraging non-Play Store-distributed Android apps to deliver malware. As such, users should not install apps outside the Play Store and be wary of social engineering techniques that might get people to install an overly-permissive Android app that could prove to be a security risk.

