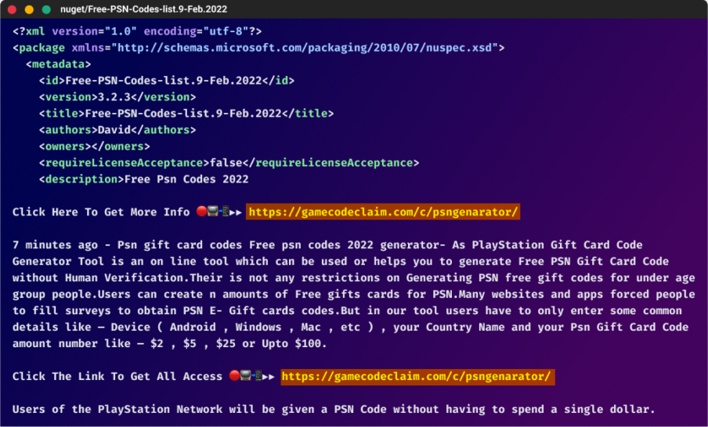
Massive Phishing Campaign Bombards Open Source Repositories With Over 144K Packages

Joint research conducted by cybersecurity firms Checkmarx and Illustria has revealed a massive phishing campaign that flooded open source repositories with over 144,000 packages. Unlike many other campaigns that involve the distribution of software packages, this newly discovered campaign didn’t attempt to distribute packages containing malicious payloads. Instead, the packages functioned as a ploy to direct users to a chain of phishing, survey, and e-commerce sites.
The threat actors uploaded these phishing packages to three different package repositories: NPM, NuGet, and PyPi. The packages in question were uploaded by a set of user accounts with names following a shared pattern, with each account publishing the same number of packages, suggesting that the publishing of these packages was automated.
The threat actors uploaded these phishing packages to three different package repositories: NPM, NuGet, and PyPi. The packages in question were uploaded by a set of user accounts with names following a shared pattern, with each account publishing the same number of packages, suggesting that the publishing of these packages was automated.
The packages themselves had names related to hacking, cheats, and free resources, such as social media followers or in-game currency. The campaign was designed to lure people in with these package names and leverage the credibility of legitimate package repositories to trick people into downloading the packages. These packages contained links to websites presented as offering the same services advertised in the package names.
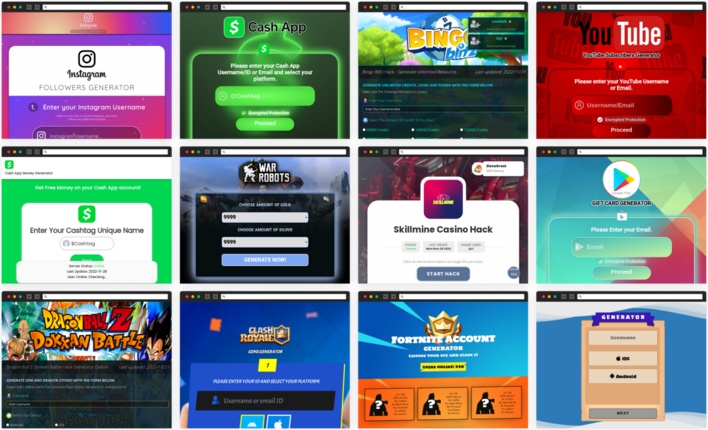
Users who opened these links found websites that appeared to offer the expected services. However, under the guise of offering these services, each website asked users to enter their login credentials for the related accounts. These seemingly legitimate login prompts functioned to steal victims’ account credentials. Upon receiving these credentials, the websites appeared to process this information in order to generate the advertised “gifts,” but would then ask for “human verification.”
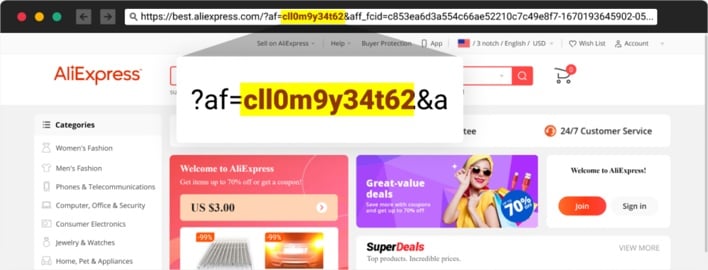
This supposed verification process redirected users through a chain of various survey sites, eventually dumping users out onto legitimate e-commerce sites. The redirections to e-commerce sites included referral codes in the URLs as a means of monetization for the threat actors behind this campaign. If victims went on to make purchases on these sites while the referral codes were active, the threat actors would receive referral awards. Thus, redirecting users from the original phishing sites served both as a distraction from the theft of victims’ login credentials and a secondary exploitation scheme.
The offending phishing packages have since been removed from the repositories, except in the case of NuGet, where the packages were unlisted from the repository’s search results. These unlisted packages are still available, but not easily accessible. Users should nonetheless stay vigilant when browsing package repositories. The automated nature of this campaign means that threat actors may very well conduct a similar phishing campaign given the relative ease of doing so.
The offending phishing packages have since been removed from the repositories, except in the case of NuGet, where the packages were unlisted from the repository’s search results. These unlisted packages are still available, but not easily accessible. Users should nonetheless stay vigilant when browsing package repositories. The automated nature of this campaign means that threat actors may very well conduct a similar phishing campaign given the relative ease of doing so.