Beware Of Phishing Emails Posing As Security Updates In Wake Of Colonial Pipeline Attack

Colonial Pipeline was content to fly under the radar as the top fuel pipeline in the United States, but then it was hit by a ransomware attack that severely disrupted operations, and its name was plastered across headlines. Looking to take advantage of the situation and newfound name recognition, hackers are hoping to dupe victims with phishing emails masquerading as required system updates.
This is part of the fallout from the attack on a piece of critical infrastructure, and the unwanted notoriety that comes with it. Colonial Pipeline operates over 5,500 miles of pipe delivering 100 million gallons of fuel across 14 different states and seven airports. The attack led to a temporary shortages of gasoline, as well as a spike in fuel costs at the pump.
Colonial Pipeline reportedly shelled out $5 million in extorted funds to the hackers responsible, in exchange for a decryption tool so that it could recover its data and get back to normal operations. Now in the wake of it all, there is a phishing campaign aimed at tricking office workers into installing malware, under the guise of being a mandatory system update sent by company officials.
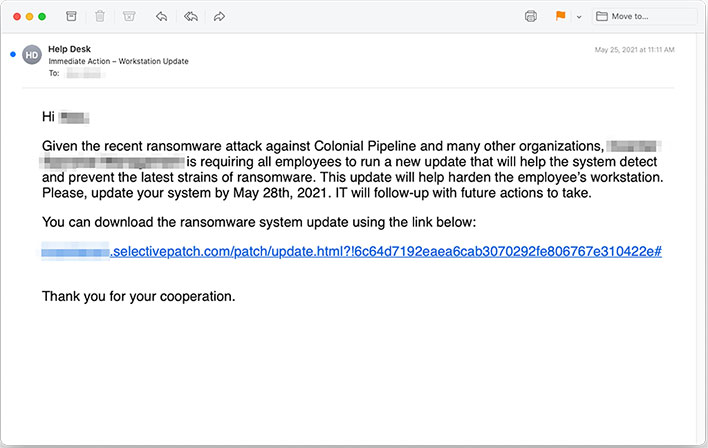
Here's a look at an example email...
The fraudulent emails come from newly created domains that, at a glance, may appear legitimate. The attackers registered them with NameCheap, a registrar that is apparently popular among hackers because of the low costs and its acceptance of Bitcoin as payment.
Customized attacks send users to a website with their company's logo and images, so as not to arise suspicion. Victims are then instructed to download a file called "Ransomware_Update.exe" and then install it. That would be a big mistake. It's not actually a security update, but a penetration tool that malicious actors use to install malware, including ransomware.
There's a security report floating around suggesting that around a third of all ransomware attacks leverage Cobalt Strike. It is popular and unfortunately effective, and is now being used to target workers who may be more familiar with Colonial Pipeline and the concept of ransomware because of recent events.
This latest ransomware phishing campaign also preys on people's desire to assist their IT team with keeping their systems secure. So, it is easy to imagine this being an effective campaign, unfortunately, though it is not clear how many people have fallen for it.
If you are an IT admin, you may want to send out a memo alerting workers to this type of fraud, and offer up tips on best practices to avoid ransomware in general. And on the flip side, if anyone receives an unexpected email instructing them to install software, they should check directly with IT personnel first.