This Sinister Pokémon NFT Scheme Is Leaving Windows PCs Vulnerable To Attack

Cybersecurity researchers at ASEC have uncovered a threat campaign distributing remote access software under the guise of a Pokémon NFT card game. While many threat campaigns distribute Remote Access Trojans (RATs) that operate in the background to grant threat actors access to compromised systems, this particular scheme exists to distribute another kind of RAT, namely Remote Administration Tools. Rather than being malware, these legitimate tools provide users with a graphical user interface (GUI) and remote desktop functionality. However, some threat actors abuse remote desktop software as a means to access and compromise their targets’ machines, and, in this case, threat actors are leveraging NetSupport Manager for malicious purposes.
NetSupport Manager by itself is a set of non-malicious Remote Administration Tools with remote desktop functionality, but unknown threat actors have bundled this legitimate software into a malicious package that the ASEC researchers call “NetSupport RAT”. This package installs NetSupport Manager and configures it to run at start and connect to a NetSupport server controlled by the threat actors. Once the software establishes a connection to this server, the threat actors are able to remotely control the compromised system, enabling them to execute arbitrary commands, access clipboard contents, observe user actions, and exfiltrate files and web browser history.
NetSupport Manager by itself is a set of non-malicious Remote Administration Tools with remote desktop functionality, but unknown threat actors have bundled this legitimate software into a malicious package that the ASEC researchers call “NetSupport RAT”. This package installs NetSupport Manager and configures it to run at start and connect to a NetSupport server controlled by the threat actors. Once the software establishes a connection to this server, the threat actors are able to remotely control the compromised system, enabling them to execute arbitrary commands, access clipboard contents, observe user actions, and exfiltrate files and web browser history.
For at least two years, threat actors have been distributing NetSupport RAT through various methods, including spam emails and hacked WordPress blogs. The particular campaign identified by ASEC seems to have begun around December 2022 and seeks to distribute the malicious package through fraudulent installers for both legitimate and fake software. These installers are disguised with icons corresponding to the imitated software, but install NetSupport RAT rather than the expected software.
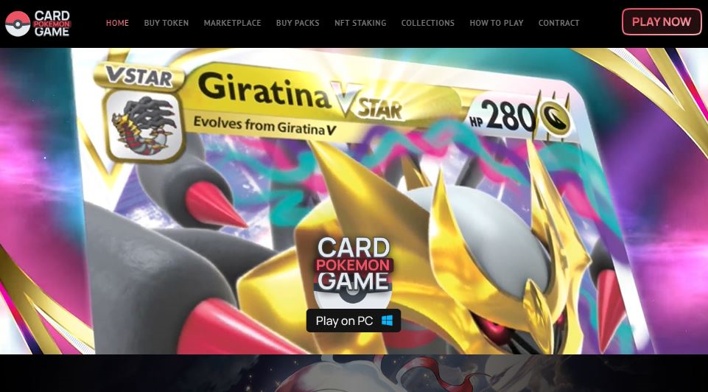
The researchers discovered versions of the installer with the Microsoft Visual Studio logo, but don’t know the original source of these samples. However, they did find websites promoting a bogus Pokémon non-fungible token (NFT) card game that serves as a method to trick victims into installing NetSupport RAT. The “Play on PC” button on these websites downloads a version of the malicious package installer disguised with an icon for the fake game and bearing the name “PokemonBetaGame.exe.” When run, this executable infects systems with NetSupport RAT.
While the websites distributing this malicious package are no longer running at the domains identified by the ASEC researchers, that doesn’t mean the threat campaign is over. In order to avoid infecting their systems with malware, users should avoid downloading legitimate software from unfamiliar sources and should be wary of downloading games that can’t be verified as real.
The researchers discovered versions of the installer with the Microsoft Visual Studio logo, but don’t know the original source of these samples. However, they did find websites promoting a bogus Pokémon non-fungible token (NFT) card game that serves as a method to trick victims into installing NetSupport RAT. The “Play on PC” button on these websites downloads a version of the malicious package installer disguised with an icon for the fake game and bearing the name “PokemonBetaGame.exe.” When run, this executable infects systems with NetSupport RAT.
While the websites distributing this malicious package are no longer running at the domains identified by the ASEC researchers, that doesn’t mean the threat campaign is over. In order to avoid infecting their systems with malware, users should avoid downloading legitimate software from unfamiliar sources and should be wary of downloading games that can’t be verified as real.

