Microsoft Confirms Multiple Critical 0-Day Flaws In Exchange Server

On Wednesday this week, cybersecurity firm GTSC released a blog post titled “New Attack Campaign Utilized A New 0-Day RCE Vulnerability On Microsoft Exchange Server,” which outlined detected exploit requests similar to the ProxyShell vulnerability of 2021. Shortly thereafter, Microsoft dove into triage mode and assigned CVE-2022-41040 and CVE-2022-41082, a server-side request forgery and remote code execution vulnerability, respectively. However, it was noted that to exploit either vulnerability, an attacker must have valid credentials for a non-admin user on the Exchange server.
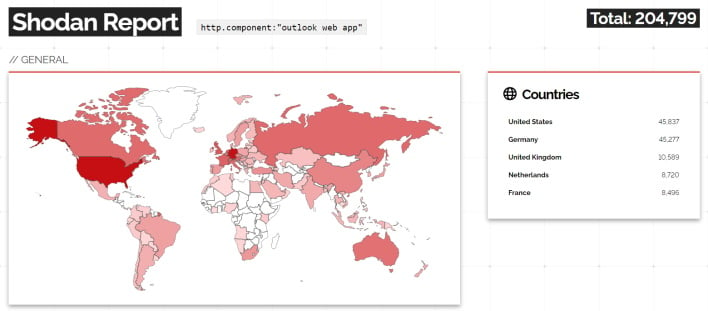
Cybersecurity researcher and purveyor of vulnerability names and logos Kevin Beaumont quickly dubbed this issue “ProxyNotShell” because “it is the same path and SSRF/RCE pair from [ProxyShell in 2021]… but with authentication.” He further explained that this problem only affects those who run Microsoft Exchange on-premise and don’t have the Outlook Web App (OWA) facing the internet. However, using Shodan, an internet-connected device search engine, it is reported that there are potentially 204,000 exposed OWA pages meaning these organizations should assess their exposure and potentially mitigate the issue.
To this end, Microsoft provides three options for mitigation on its blog, the first of which is effectively “sit tight,” as customers with the Exchange Server Emergency Mitigation Service enabled will have mitigations pushed automatically. Beyond this, Microsoft has created a script that customers can deploy, or administrators can create URL rewrite rules themselves. Microsoft also notes that Exchange Online customers need not take any action, but Beaumont counters this and explains that Exchange Hybrid servers are potentially vulnerable and should be updated and secured.
It should also be noted that there is information available that can help admins discover if either vulnerability has been deployed against their infrastructure. Hopefully, with all this coverage and mitigations now rolling out, this problem will not spiral out of control over the weekend. Otherwise, if you or a beloved admin has been affected by ProxyNotShell linked to Exchange exposure, you may be entitled to financial compensation.